BlueNoroff APT group using new ways to bypass MotW protection
The BlueNoroff subcluster of the Lazarus Group has adopted new techniques that allow it to bypass Windows’ Mark of the Web protections.
MotW
The Windows Mark of the Web (MotW) is a security feature that helps protect users from malicious content that is downloaded from the internet. It does this by adding a security mark, or “mark of the web”, to any file that is downloaded from the internet or from a network location that is not considered trusted.
This mark is added to the file’s metadata and can be used by security software to identify the file as potentially dangerous.
When a file with the MotW is opened, Windows will display a warning message to the user, informing them that the file has come from an untrusted source and may be dangerous. This warning serves as a reminder to the user to be cautious when opening files from unknown sources, and helps prevent accidental execution of malicious content.
The MotW feature is designed to work in conjunction with other security measures, such as antivirus software and firewall protection, to help protect users from online threats. It is an important part of the security infrastructure in Windows, and helps prevent the spread of malware and other malicious content on the internet.
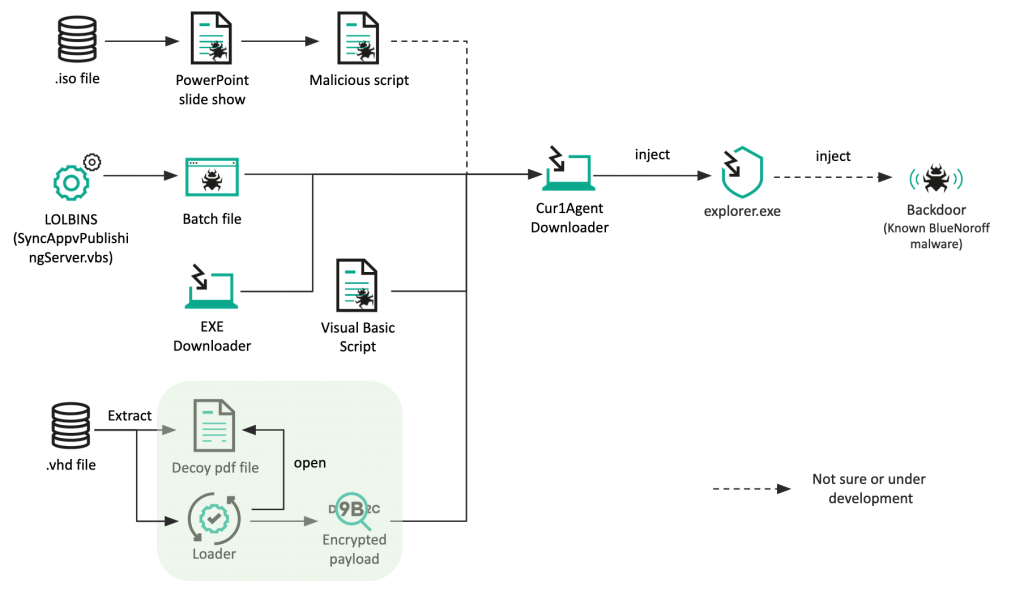
The Technique
These new techniques include the use of optical disk image and virtual hard disk file formats as part of its infection chain.
BlueNoroff has been found to create fake domains impersonating venture capital companies and banks, most of which are located in Japan. The group, which is also known as APT38, Nickel Gladstone, and Stardust Chollima, is part of the larger Lazarus threat group and has financial rather than espionage motivations.
It has been associated with high-profile cyber attacks against the SWIFT banking network between 2015 and 2016, including the Bangladesh Bank heist, and has more recently focused on cryptocurrency entities to generate illicit revenue.
Kaspersky has identified two methods being used by BlueNoroff to deliver its payload, one involving spear-phishing emails with ISO files containing a PowerPoint file and Visual Basic Script, and the other involving the exploitation of a living-off-the-land binary to retrieve a second-stage downloader that fetches and executes a remote payload. The exact backdoor delivered is not clear, but it is believed to be similar to one used in previous SnatchCrypto attacks.
The group’s use of Japanese file names and fraudulent domains disguised as Japanese venture capital companies suggests that financial firms in Japan may be a target.