MasquerAds: a new Malvertising campaign via Google Ads
A new cyber attack campaign called MasquerAds is targeting users who are searching for popular software by using Google Ads to serve malware-infected variants of the software. These malware-infected versions, which include Raccoon Stealer and Vidar, are being served through the use of credible websites with typosquatted domain names.
These websites are then surfaced on top of Google search results in the form of malicious ads, through the hijacking of searches for specific keywords in order to trick unsuspecting users into downloading malicious programs or potentially unwanted applications.
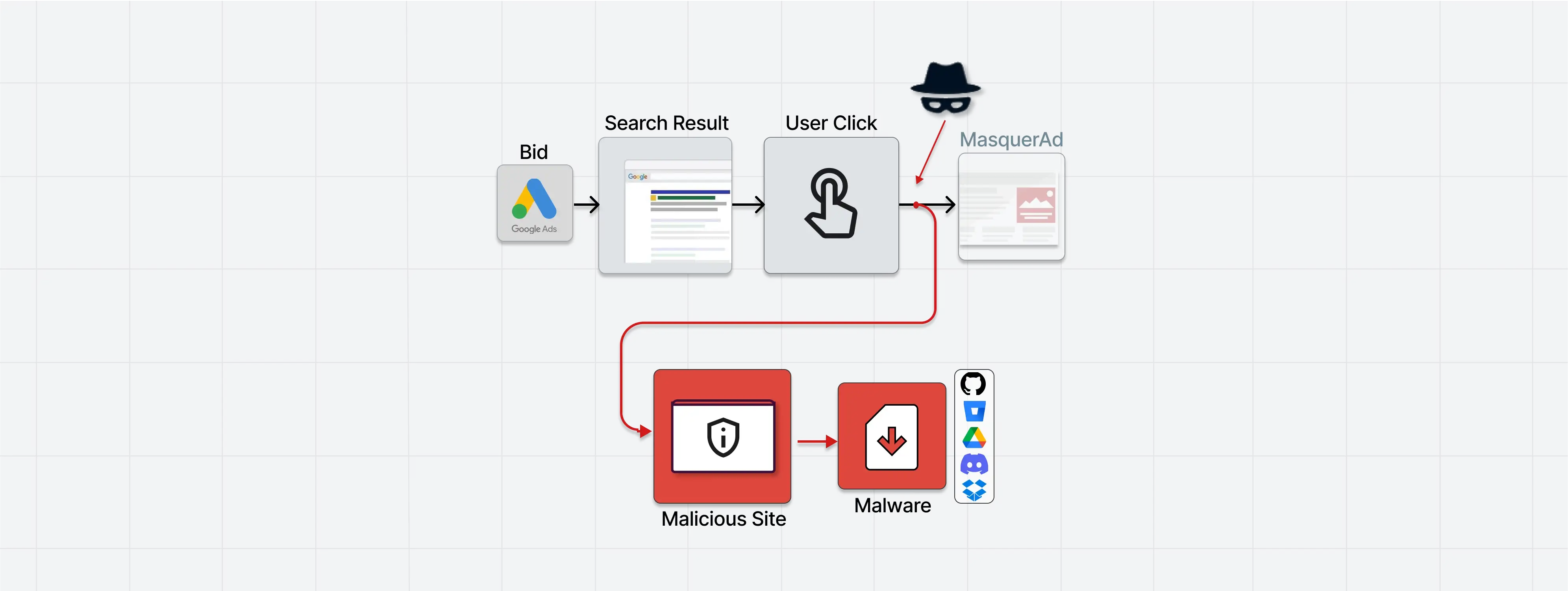
The MasquerAds campaign, discovered by Guard.io experts, has mainly targeted users in Canada and the US, and has mainly been used to proliferate cryptocurrency miners and the Vidar information stealer. The campaign is believed to be carried out by a threat actor known as Vermux, which is reportedly “abusing a vast list of brands and keeps on evolving.”
It is not the first time that the Google Ads platform has been used to dispense malware.
In the past, the platform has been leveraged to deploy BATLOADER, which was then used to drop Royal ransomware. Malicious actors have also used malvertising techniques to distribute the IcedID malware through cloned web pages of well-known applications such as Adobe, Brave, Discord, LibreOffice, Mozilla Thunderbird and TeamViewer.
IcedID is a noteworthy malware family that is capable of delivering other payloads, including Cobalt Strike, and has the ability to enable attackers to perform highly impactful follow-through attacks that can lead to total system compromise, such as data theft and crippling ransomware.
The findings of this MasquerAds campaign come at a time when the US Federal Bureau of Investigation (FBI) has warned that
“cyber criminals are using search engine advertisement services to impersonate brands and direct users to malicious sites that host ransomware and steal login credentials and other financial information.”
IOCs
Miscellaneous Active Domains and IPs During 11–12/2022 Including malware sample links and virus-total analysis: https://gist.github.com/guardiolabs/2178c54367d20b0655b5cc5e9d297760
Vermux-specific operation During 11–12/2022: https://gist.github.com/guardiolabs/7f46d1adda8b0c08e76f23d9fab27fe9