A brief history of malware
These days I am finishing the first draft of a new book of the “Little Handbooks” series, dedicated to Malware Analysis. One of the first chapters is a brief history of computer viruses.
Comments and feedback are welcome!
Malware is a term used to describe malicious software that is designed to harm or exploit computer systems. It can take various forms, such as viruses, worms, trojans, rootkits, ransomware, and adware, and can be used for various purposes, such as stealing data, disrupting services, or extortion.
The history of malware can be traced back to the early days of computing, when the first known computer viruses were created. However, it was not until the rise of the personal computer (PC) and the internet that malware became a significant threat. The proliferation of PCs and the internet created new opportunities for malware to spread and to target a larger and more diverse audience.
In this chapter, we will examine the early history of malware, the birth of the PC, the rise of the internet, the emergence of mobile malware, and the rise of ransomware. We will also discuss the trends and challenges of malware and its impact on society. By understanding the history of malware, we can gain insight into its evolution and future direction and be better prepared to defend against it.
Early history of malware
Malware, short for malicious software, refers to any software designed to harm or exploit computer systems. While the term “malware” was not coined until the 1990s, the concept of malicious code has a long history that dates back to pre-digital times.
Pre-digital era: Malicious code in literature and folklore
One of the earliest references to malicious code can be found in the Greek myth of the Trojan Horse. According to the story, the Greeks built a giant wooden horse and presented it as a gift to the Trojans, who were at war with them.
Unknowingly, the Trojans brought the horse into their city, where it contained a group of Greek soldiers who emerged during the night and opened the gates for the rest of the Greek army, leading to the fall of Troy. The Trojan Horse has since become a metaphor for a malicious program that disguises itself as something benign in order to gain access to a system.
In the 16th century, the play “Doctor Faustus” by Christopher Marlowe includes a reference to a “machine or engine, which will make a man invisible”. This is often cited as an early example of a “logic bomb”, a type of malware that is triggered by a specific condition or event, such as a certain date or the deletion of a file.
Early computers: First instances of malware
As computers became more prevalent in the 20th century, the first instances of malware began to appear.
| DEC (Digital Equipment Corporation) PDP-10 CPU, model KI-10 |
One of the earliest known examples is the ”Creeper” program, which was created in 1971 by Bob Thomas. Creeper was a simple self-replicating program that infected DEC PDP-10 computers and displayed the message “I’M THE CREEPER: CATCH ME IF YOU CAN”.
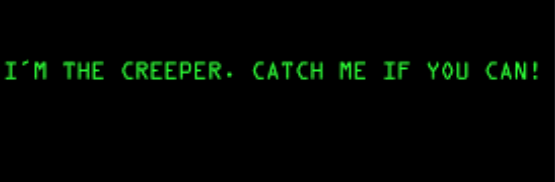 |
|---|
| Text of the Creeper worm. |
It was followed by the “Reaper” program, which was designed to remove Creeper from infected systems.
Other early examples of malware include the “Elk Cloner” virus, which infected Apple II computers in 1982, and the “Brain” virus, which targeted **IBM PC **systems in 1986. These viruses were primarily spread through floppy disks and were relatively simple in nature, but they marked the beginning of the modern era of malware.
The emergence of personal computers
The birth of the PC: Early malware targeting PC systems
With the emergence of personal computers (PCs) in the 1980s, malware began to evolve and target these systems.
The first PC-based viruses, such as the “Brain” virus, appeared in 1986 and were primarily spread through floppy disks. These viruses were relatively simple in nature, but they marked the beginning of a new era of malware that would continue to evolve and grow more sophisticated over time.
 |
|---|
| The boot sector of an infected floppy |
One of the most notable early PC **viruses was the “Michelangelo” virus, which was discovered in 1992. Michelangelo was a boot sector virus that was triggered on **March 6th (Michelangelo’s birthday) and caused infected computers to display a message stating that the system had been infected. It was estimated that Michelangelo could potentially infect up to 5% of the world’s PCs, causing widespread panic and leading to media coverage of the incident.
Other notable early PC viruses include the “Jerusalem” virus, which was discovered in 1987 and targeted executable files, and the “Melissa” virus, which was discovered in 1999 and spread through email attachments. These and other early PC viruses were primarily spread through physical media such as floppy disks and CDs, but the rise of the internet in the late 1990s would pave the way for a new generation of malware that could spread much faster and more effectively.
The rise of the internet: Malware spreads online
With the rise of the internet in the late 1990s, malware began to spread in new and more effective ways. The internet provided a global network for the transmission of malware, allowing it to reach a wider audience and cause greater damage.
One of the first notable internet-based malware outbreaks was the “Love Bug” or “ILOVEYOU” virus, which was discovered in 2000.
 |
|---|
| ILOVEYOU screenshot |
The Love Bug was a worm that spread through email attachments and infected millions of computers around the world, causing an estimated $10 billion in damages.
Other notable internet-based malware include the “Code Red” worm, which was discovered in 2001 and targeted Microsoft IIS servers, and the “Sasser” worm, which was discovered in 2004 and exploited a vulnerability in Windows XP systems. These and other internet-based malware demonstrated the potential for significant global impact and highlighted the need for effective cyber security measures.
The rise of the internet also led to the emergence of new types of malware, such as phishing attacks and malicious websites. Phishing attacks involve the use of fake emails or websites to trick users into revealing sensitive information, such as login credentials or financial details. Malicious websites, also known as “drive-by downloads”, are sites that automatically download malware onto a user’s computer when visited. These and other internet-based threats continue to pose a significant risk to individuals and organizations today.
Modern malware trends
The rise of mobile malware
With the proliferation of smartphones and other mobile devices, malware has increasingly targeted these platforms. Mobile malware refers to any software that is designed to harm or exploit mobile devices. It can take many forms, including viruses, worms, trojans, and ransomware, and it can be spread through various means, such as app downloads, SMS messages, and malicious websites.
One of the first notable instances of mobile malware was the “Cabir” worm, which was discovered in 2004 and targeted Nokia Series 60 phones.
Cabir was a proof-of-concept worm that could spread over Bluetooth connections and display the message “Caribe” on infected phones. It was followed by other mobile worms, such as “Commwarrior” and “Lasco”, which targeted various mobile platforms and spread through MMS messages.
 |
|---|
| A Nokia 3650 |
As smartphones became more prevalent, mobile malware began to evolve and become more sophisticated. In 2011, the “Android.FakePlayer” trojan was discovered, which was capable of disguising itself as a legitimate Android app and downloading additional malware onto the device. In 2013, the “Snapchat” trojan was discovered, which targeted Android devices and stole sensitive information such as login credentials and phone numbers.
Mobile malware continues to be a significant threat today, with new strains appearing regularly. It is important for mobile users to be aware of the risks and take steps to protect their devices, such as installing antivirus software and avoiding suspicious app downloads or websites.
The emergence of ransomware
Ransomware is a type of malware that encrypts a victim’s files and demands a ransom from the victim to restore access. It typically spreads through phishing attacks or malicious software downloads and can have a significant impact on individuals and organizations.
One of the first instances of ransomware was the “PC Cyborg” or “AIDS” trojan, which was discovered in 1989. PC Cyborg infected computers and displayed a message stating that the user’s license had expired and that they needed to pay a fee to obtain a new one. It was followed by other early ransomware, such as the “Gpcode” trojan, which was discovered in 2006 and used strong encryption to lock users’ files.
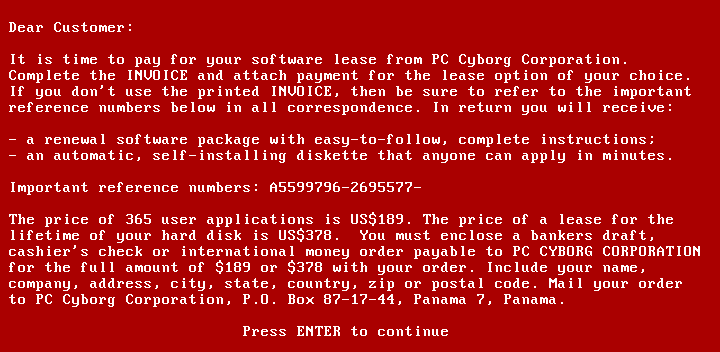 |
|---|
| Message after activation of AIDS |
Ransomware gained widespread attention in 2013 with the emergence of the “CryptoLocker” malware, which infected millions of computers and demanded a ransom in exchange for the decryption key.
CryptoLocker was particularly effective because it used strong encryption and demanded payment through anonymous online payment systems.
It was followed by other high-profile ransomware, such as “Locky” and “WannaCry“, which caused significant damage and disrupted the operations of various organizations.
 |
|---|
| Screenshot of the ransom note left on an infected system |
The emergence of ransomware has led to a significant increase in cyber extortion attacks, with ransom demands ranging from a few hundred to several thousand dollars. It is important for individuals and organizations to be aware of the risks and take steps to protect themselves, such as maintaining regular backups and implementing strong security measures.
State-sponsored and APT attacks
State-sponsored and Advanced Persistent Threat (APT) attacks are a type of malware that are typically used for cyber espionage or sabotage.
They are usually sophisticated and well-funded, and they often target specific organizations or individuals.
One of the most well-known state-sponsored attacks is the “Stuxnet” worm, which was discovered in 2010 and targeted industrial control systems (ICS).
Stuxnet was believed to be developed by the US and Israeli governments and was used to sabotage the Iranian nuclear program. It was a highly advanced worm that was capable of infecting air-gapped systems (systems that are physically isolated from the internet) and modifying the operation of ICS without the user’s knowledge.
Other notable state-sponsored and APT attacks include the “Red October” campaign, which was discovered in 2012 and targeted various governments and embassies, and the “Duqu” malware, which was discovered in 2011 and was believed to be related to Stuxnet.
These and other state-sponsored and APT attacks have demonstrated the potential for significant damage and have raised concerns about the role of governments in cyber warfare.
Dark web, underground markets and Malware-as-a-Service
The dark web is a hidden portion of the internet that can only be accessed using specialized software, such as the TOR network. It is a largely anonymous network that is used for a variety of purposes, including the sale of illegal goods, services an malware.
The dark web is home to a variety of underground markets, where individuals can buy and sell various items, including drugs, weapons, and stolen data. It is also a hub for the sale of *malware, **usually sold as a *service.
Malware-as-a-Service (MaaS) refers to the delivery of malware through an online service, typically on a subscription basis. With MaaS, cybercriminals can easily obtain and deploy malware without having to develop it themselves, making it a convenient and accessible option for those with limited technical skills or resources. MaaS offerings often include various types of malware, such as trojans, worms, and ransomware, as well as support and updates to ensure the effectiveness of the malware. MaaS has become a popular choice for cybercriminals, as it allows them to scale and automate their attacks, and to evade detection and attribution. It has also made it easier for inexperienced or amateur hackers to carry out cyber attacks, increasing the threat landscape and the need for effective malware analysis and detection techniques.
One of the most well-known dark web marketplaces is the “Silk Road”, which was launched in 2011 and operated until 2013, when it was shut down by the FBI. The Silk Road was a notorious marketplace for the sale of illegal goods and services, including malware and hacking tools. It was believed to have had millions of users and to have generated hundreds of millions of dollars in sales.
Other notable dark web marketplaces include “Agora” *and *“Evolution”, which were also shut down by law enforcement agencies. These and other underground markets have demonstrated the scale and scope of the illegal activities that take place on the dark web and the need for effective law enforcement efforts to combat them.