3 PyPI packages discovered spreading malware to developers systems
A threat actor known as Lolip0p has uploaded three rogue packages to the Python Package Index (PyPI) repository, which are designed to drop malware on compromised developer systems.
According to a report by Fortinet the packages, named colorslib, httpslib and libhttps, were uploaded by the author between January 7 and January 12, 2023, and have since been removed from the PyPI repository, but not before they were cumulatively downloaded over 550 times.
The modules come with identical setup scripts that are designed to invoke PowerShell and run a malicious binary (“Oxzy.exe”) hosted on Dropbox, which once launched, triggers the retrieval of a next-stage, also a binary named update.exe, that runs in the Windows temporary folder.
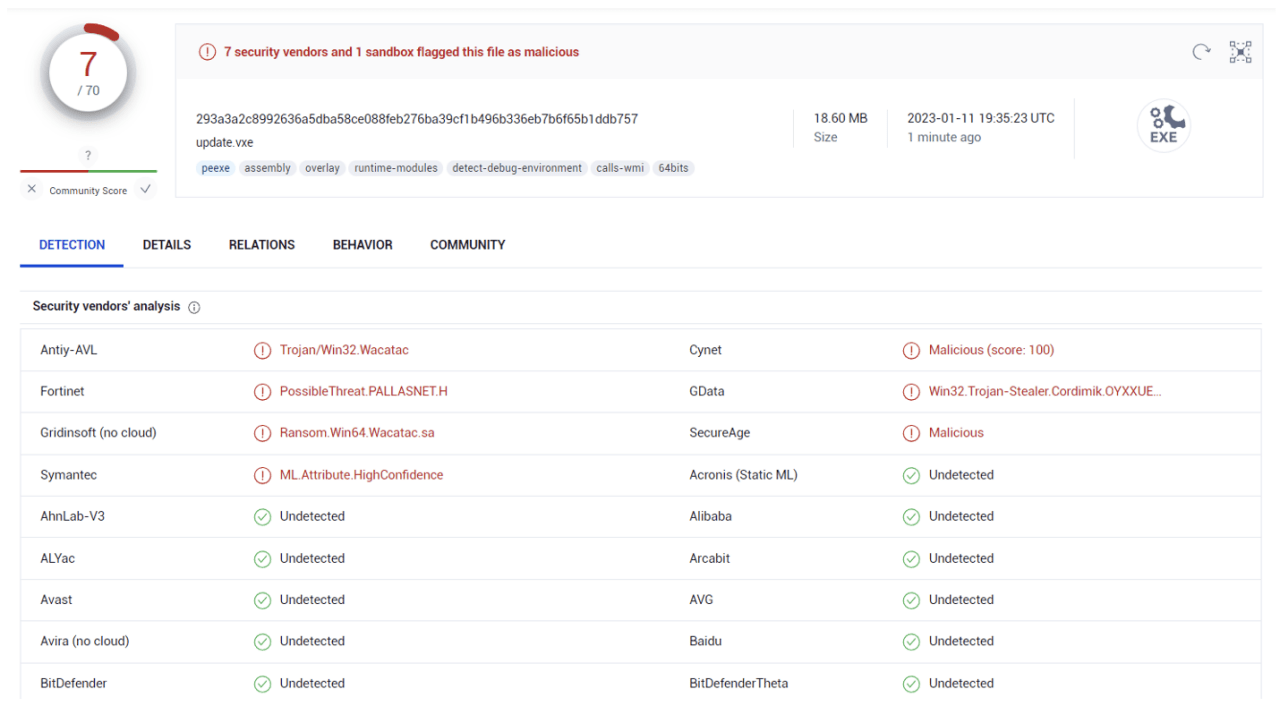
The executable update.exe is flagged by antivirus vendors as an information stealer that’s also capable of dropping additional binaries, one of which is detected by Microsoft as Wacatac.
IOCs
Oxzy.exe
- 8dc8a9f5b5181911b0f4a051444c22e12d319878ea2a9eaaecab9686e876690b
update.exe
- 293a3a2c8992636a5dba58ce088feb276ba39cf1b496b336eb7b6f65b1ddb757
SearchProtocolHost.exe
- 123fd1c46a166c54ad66e66a10d53623af64c4b52b1827dfd8a96fdbf7675638
Malicious URLs
- https://dl[.]dropbox[.]com/s/mkd3enun97s8zag/Oxzy[.]exe?dl=0