Abusing GitHub Codespaces : a new way for malware distribution
Codespaces is a development environment that allows developers to easily set up, configure, and collaborate on projects from within GitHub.
It allows users to customize their project by committing configuration files to their repository, which creates a repeatable configuration for all users of the project. Each codespace runs on a virtual machine hosted by GitHub.
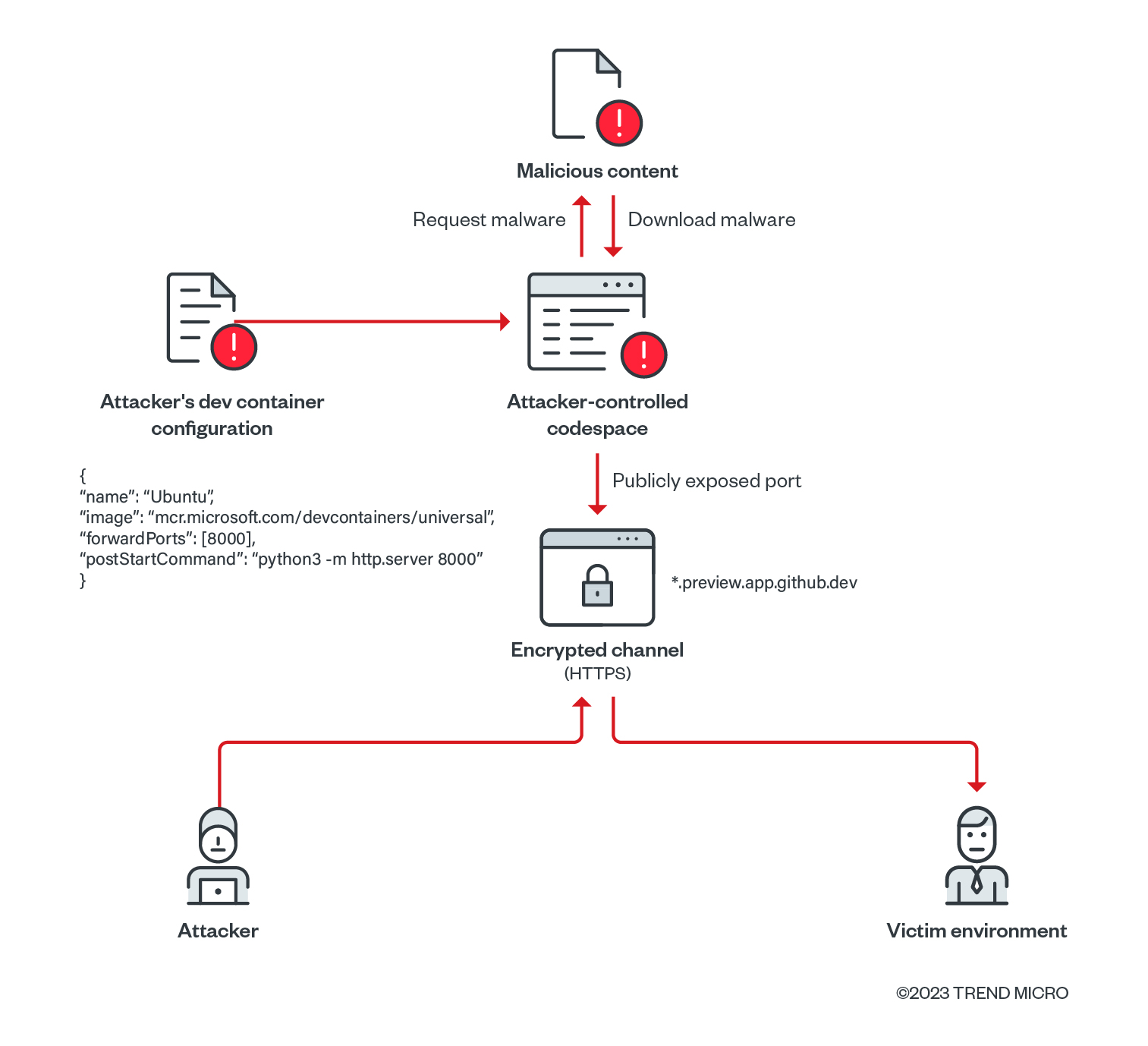
Trend Micro researchers have found a way to exploit a legitimate feature in GitHub Codespaces, a development environment, to deliver malware to victim systems.
The feature that is being targeted is the port forwarding, which allows developers to access and debug a web application that’s running on a particular port from their browser on a local machine, forwarding a port privately within an organization or publicly and making it accessible to anyone who knows the URL and the port number.
Threat actors can abuse this feature by hosting malicious content and sharing links to these resources in their attacks.
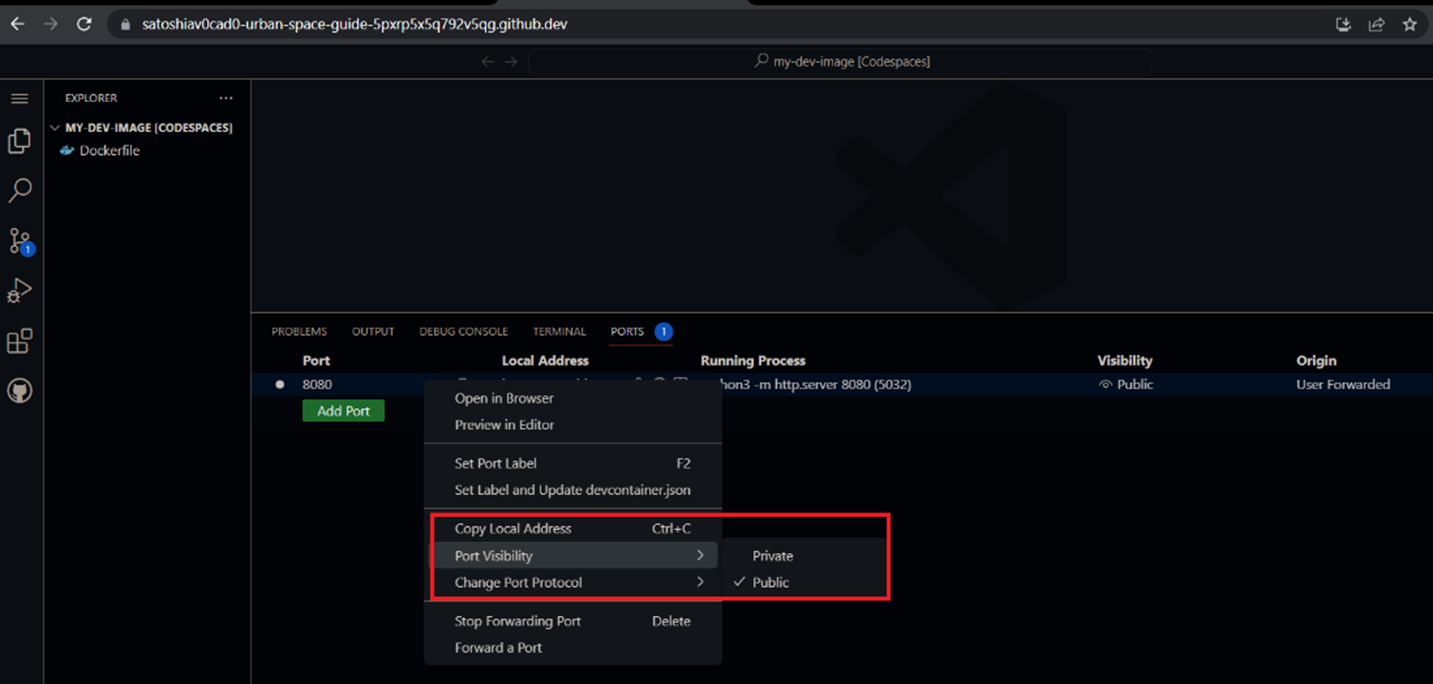
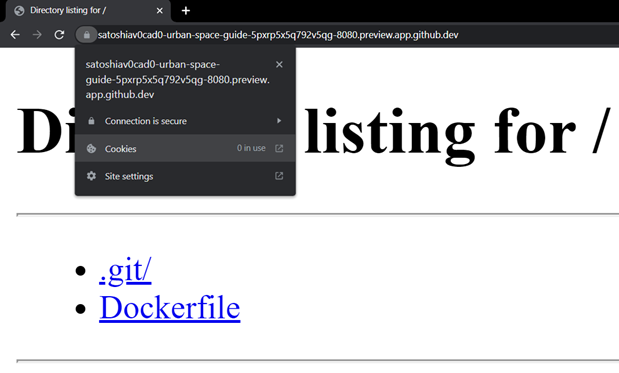
For example, they can run a Python-based HTTP server on port 8080, forward and expose the port publicly, and easily find the URL and the absence of cookies for authentication.
Additionally, GitHub Codespaces typically forwards ports using HTTP, but developers can change any port to HTTPS if needed. This is important because once a developer updates a publicly visible port to HTTPS, the port’s visibility will automatically become private.
A quick look at threat intelligence platforms like VirusTotal will show the domain having no malicious history, diminishing the chances of blocking the download of malicious files if distributed via this domain.