PY#RATION: new Python-based malware
Researchers at threat analytics firm Securonix have uncovered a new Python-based malware that has been spotted in the wild. The malware, named PY#RATION, is a remote access trojan (RAT) that gives its operators control over breached systems.
According to Securonix, the RAT uses the WebSocket protocol to communicate with its command and control (C2) server and to exfiltrate data from the infected host. The company’s technical report indicates that the malware is actively developed, as researchers have identified multiple versions of it since the PY#RATION campaign began in August.
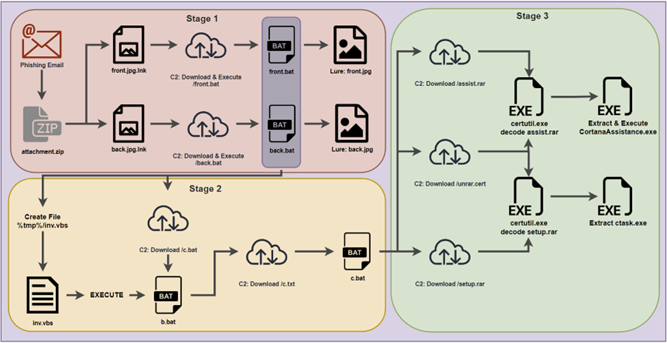
The malware is distributed via a phishing campaign using password-protected ZIP file attachments containing two .LNK files disguised as images named front.jpg.lnk and back.jpg.lnk. When run, these files appear to the victim to be the front and back of a driving licence. However, it also executes malicious code that contacts the C2 server and downloads two .TXT files, front.txt and back.txt, which are renamed to .BAT files to accommodate malware execution.

On launch, the malware creates the directories Cortana and Cortana/Setup in the user’s temporary directory and then downloads, unpacks and runs additional executables from this location.
The malware obtain persistence by adding a batch file (CortanaAssist.bat) to the user’s startup directory: it is delivered to the target as a Python RAT packed into an executable using automated packers such as pyinstaller and py2exe, which can convert Python code into Windows executables containing all the libraries needed to run.
This approach results in an inflated payload size, with version 1.0 (original) being 14MB and version 1.6.0 (latest) being 32MB. The newer version is larger because it contains additional code (+1000 lines) and a layer of Fernet encryption.
This helps the malware evade detection, and according to Securonix’s tests, version 1.6.0 of the payload was undetected by all but one antivirus engine on VirusTotal. According to the report, the malware takes advantage of Python’s built-in Socket.IO framework, which provides functions for both client and server WebSocket communication, and is used for both communication and data exfiltration.
Indicators of compromise
| SHA256/IP |
|---|
| 4d297ebe3b607eb88a6c30a74a0ad23272f44ffbcf2b49f72444048b78c6e1b4 |
| 3b445be3da961379b11af1fee71fe4513e10832f77727b3a8bbe2eb7bd60b5c3 |
| fd78f398e7cc8ced62deba213e0218d780357bcf89e01b748f8ed1e252ac3b21 |
| 4a32aa89a5250801c53d19370d98682e0561b642901bdd2987831bc983e0a544 |
| c4cf65c95e68c6d610d8735d2922f89f98a6f37257b41ba01cf8179d5947298e |
| e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 |
| 5f72c5dde7cba7071193ee7053e1adde5ea570f0c4192ac350f5835766060e5a |
| 6f8b208c3d4c1536ddf99304c880b939036a0725b1cc7fd44d768703da86fb68 |
| 180d61cbde7676c78b7b56b090f0c0d1ca5a69902ceaff26b0a1181351901011 |
| 06ecb59154d873889d92cead73238b5815358fa8a39c39868f735b24da0a3182 |
| 142b485d45344ff03c056ebf1bfe25eaeb0496338b5b2e0bb64bfef1ff81c4e6 |
| fb592d344486d7c4d15df05ce58c84717b89dda7ae5bbd1aeccf49fbc7d47646 |
| 9501b38435b960d1a1f03785681345f9f215e9b799d3ae624b989df9e32e1b38 |
| 95d2c8e6109f0ce1afb4b9d902b2f88b48ca41c6713855f3d0bf77d869a5c9a4 |
| bba407734a2567c7e22e443ee5cc1b3a5780c9dd44c79b4a94d514449b0fd39a |
| 24d66c7d5c6250403a957c282772b01c9edab85a29bcea8e0690ad7672f74ddf |
| 19c9c6c24a5f024e6469069ac8c1b0abae0ba50cb8e88b269d0a9a4c2a96265e |
| api.realproheros[.]com |
| install.realproheros[.]com |
| files.secureway[.]fun |
| login.secureway[.]fun |
| api.safeit[.]com/install/log?error= |
| 169[.]239.129.108:5555 |
| 169[.]239.129.108:5555/client/config |
| 169[.]239.129.108:5555/socket.io/?transport=polling |
| 169[.]239.129.108:5555/socket.io/?transport=websocket |