New PlugX malware variant spreads via removable USB storage devices
Cyber-security researchers at Palo Alto Networks’ Unit 42 have discovered a new variant of the PlugX malware that can infect connected USB removable media devices to spread to additional systems.
PlugX is a type of malware that is primarily used for cyber espionage and has been used in targeted attacks against organizations in various industries, including government, defense, and manufacturing. It is known for its ability to evade detection and for its use of advanced persistence mechanisms.
One of the key features of PlugX is its use of dynamic-link libraries (DLLs) for payload delivery: this allows the malware to evade detection by antivirus software, which may not be able to detect the malware if it is hidden within a legitimate DLL. Additionally, PlugX is able to evade detection by using a variety of anti-debugging and anti-virtualization techniques.
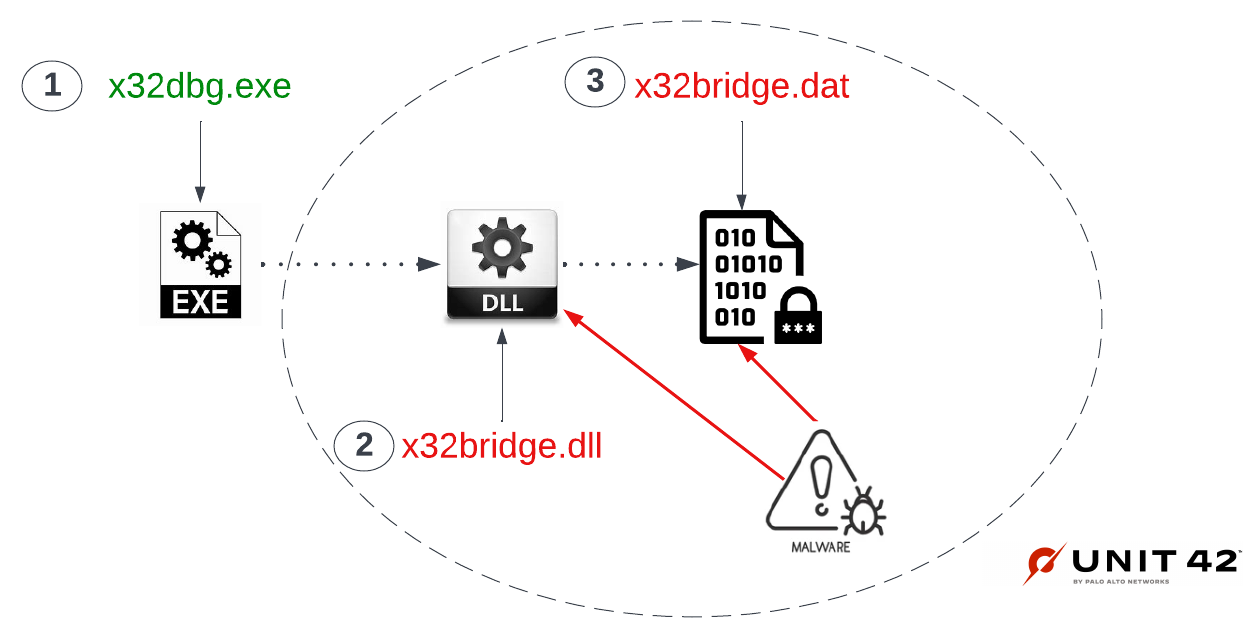
Once it has successfully compromised a system, the malware is able to gather a wide range of information, including keystrokes, screenshots, and system information. The malware is also able to upload and download files, as well as execute arbitrary code on the infected system.
PlugX has been used in targeted attacks against organizations in various countries, including the United States, Japan, and South Korea. It has been linked to a number of advanced persistent threat (APT) groups, including the group known as Deep Panda or APT 18 which is believed to be operating out of China.
This version uses a Unicode character called a non-breaking space (U+00A0) to hide files on a USB device connected to a workstation. Windows File Explorer does not display hidden items by default, so the malware remains undetected.
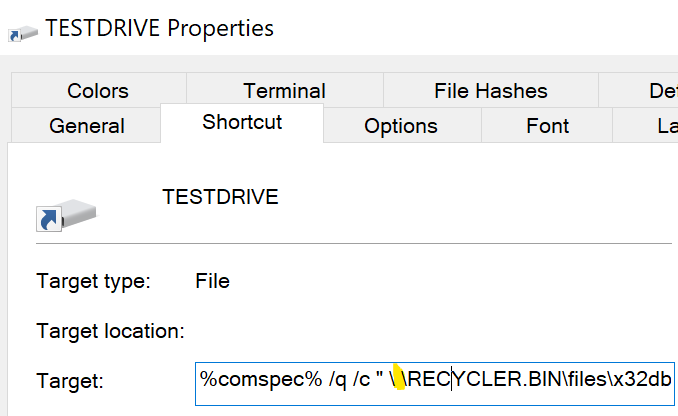
The malware also copies files from the host to another hidden folder on the USB device, indicating that attackers are attempting to exfiltrate specific files of interest from their targets and jump over air-gapped networks.
The researchers said the discovery of this sample indicates that PlugX development is still alive and well, at least among some technically skilled attackers, and remains an active threat.
Indicator of compromise
| SHA256 |
|---|
| 8ec37dac2beaa494dcefec62f0bf4ae30a6ce44b27a588169d8f0476bbc94115 |
| e72e49dc1d95efabc2c12c46df373173f2e20dab715caf58b1be9ca41ec0e172 |
| 0e9071714a4af0be1f96cffc3b0e58520b827d9e58297cb0e02d97551eca3799 |
| 39280139735145ba6f0918b684ab664a3de7f93b1e3ebcdd071a5300486b8d20 |
| 41a0407371124bcad7cab56227078ccd635ba6e6b4374b973754af96b7f58119 |
| 02aa5b52137410de7cc26747f26e07b65c936d019ee2e1afae268a00e78a1f7f |
| 2a07877cb53404888e1b6f81bb07a35bc804daa1439317bccde9c498a521644c |
| 5d98d1193fcbb2479668a24697023829fc9dc1f7d31833c3c42b8380ef859ff1 |