TrickGate: a shellcode-based packer undetected for years
TrickGate is a shellcode-based packer that has been operating successfully and undetected for over six years.
It is offered as a service to other threat actors to help hide malware payloads behind a layer of wrapper code and bypass security solutions installed on a target host.
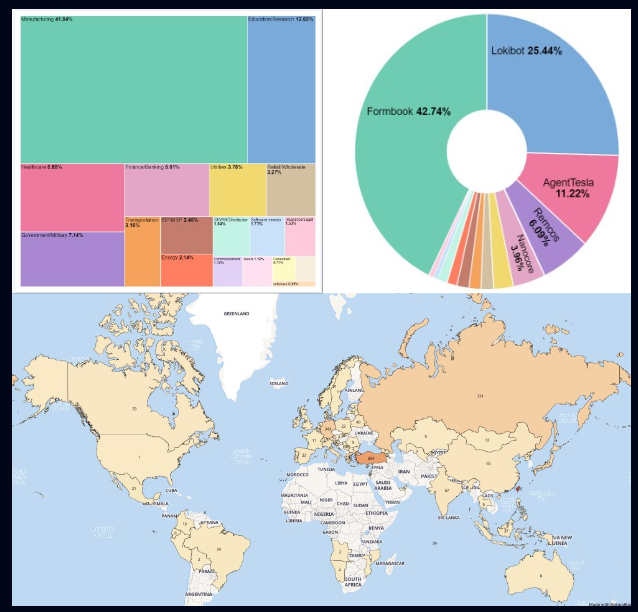
According to Check Point Research, TrickGate has primarily targeted the manufacturing sector, with lesser attacks in the education, healthcare, government and financial sectors. The most common malware used in the attacks are FormBook, LokiBot, Agent Tesla, Remcos and Nanocore,
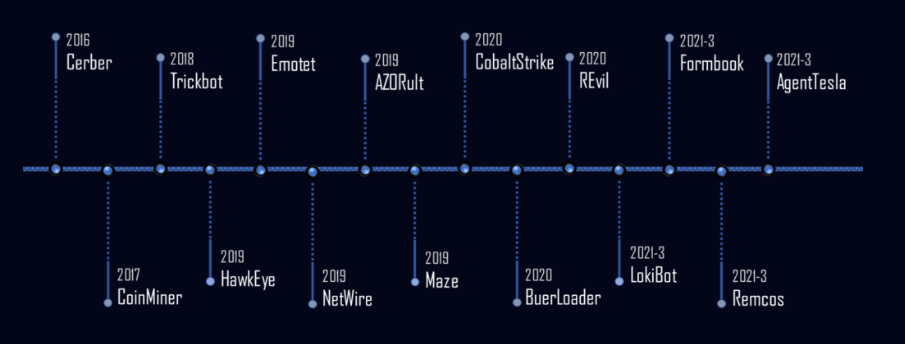
with significant concentrations reported in Taiwan, Turkey, Germany, Russia and China.
The infection chain starts with phishing emails with malicious attachments or links that lead to the download of a shellcode loader, which then decrypts and launches the actual payload in memory.
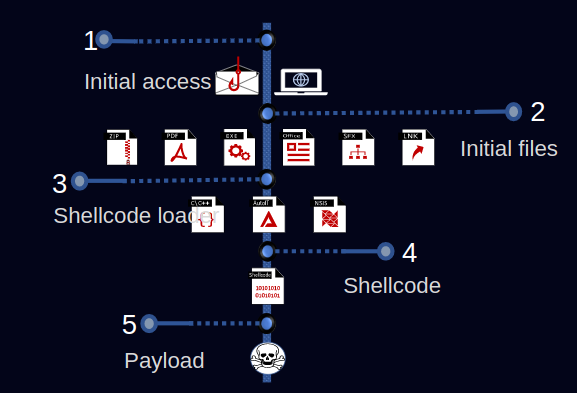
The shellcode has been updated over the years, but the injection module is the most consistent part and has been observed in all TrickGate shellcodes.
Indicator of Compromise
| SHA256 |
|---|
| 03d9cbee9522c2c8a267b7e9599a9d245c35c7ac |
| 043ae57e01ebd0a96fa30b92821b712504cfde03 |
| 1a455baf4ce680d74af964ea6f5253bbeeacb3de |
| 22f26496f2e8829af9f5cfcd79c47e03fe9a21bb |
| 24aa45280c7821e0c9e404f6ce846f1ce00b9823 |
| 30e0181a018fa7dcbd2344dc32adcf77cf840ebe |
| 3437ea9b7592a4a05077028d54ef8ad194b45d2f |
| 3817bad277aa50016e08eed35e92d4a3b5247633 |
| 4380044a9517a08514459005836c5f92e4a33871 |
| 4f6fa448454b581d6c8e7aa6ed3ef72e66062bf8 |
| 666c5b23521c1491adeeee26716a1794b09080ec |
| 75d999d431819311abf8bd048cd084acdcd5f4e1 |
| 7f456f8b01fc8866aeed4678a14479b6eaa62fed |
| 975629358bfbba0344ef0dae4d22697ceb2a32b4 |
| 977800bd7be3c5c9f2c0dac7f4806e586d8f7b1a |
| 9f20d00b4ec898a33e130720d4d29e94070e1575 |
| a1f73365b88872de170e69ed2150c6df7adcdc9c |
| a661541c4cbeb1db859f6cec6c53979b5633c75e |
| afbe838c881e5b223351ff8fa05ddeb3678581ba |
| b2d58dfee71ce9c509fab1f00ce04c9526c60695 |
| e6dccf4b1fc5ab116b6bc1321346b35dbf42f387 |
| fa5c79321dd4cc2fea795d6ebe2e823abe33ca6f |