GuLoader: new version uses Nullsoft Scriptable Install System
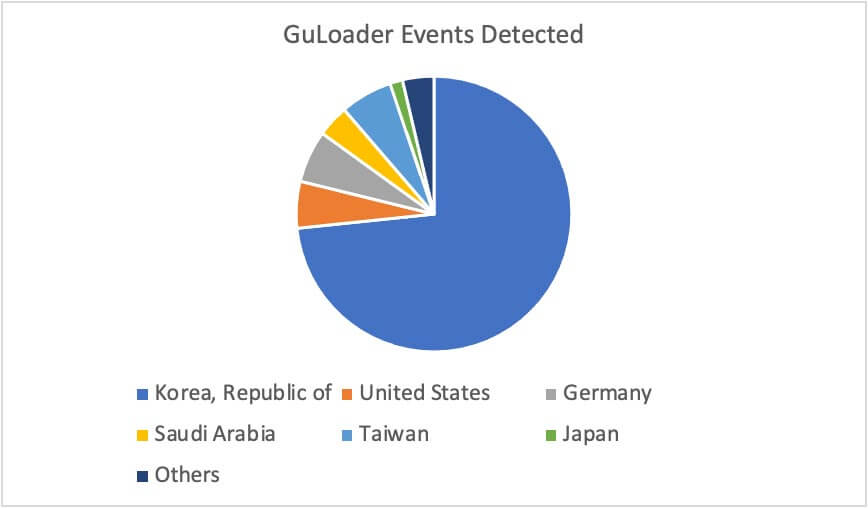
Several e-commerce industries in South Korea and the United States are being targeted by a GuLoader malware campaign, according to a report from cybersecurity firm Trellix.
The attack is notable for its transition from using malware-laden Microsoft Word documents to using NSIS executables to load the malware. Other countries targeted in the campaign include Germany, Saudi Arabia, Taiwan and Japan.
NSIS, or Nullsoft Scriptable Install System, is a script-driven open source system used to develop installers for the Windows operating system.
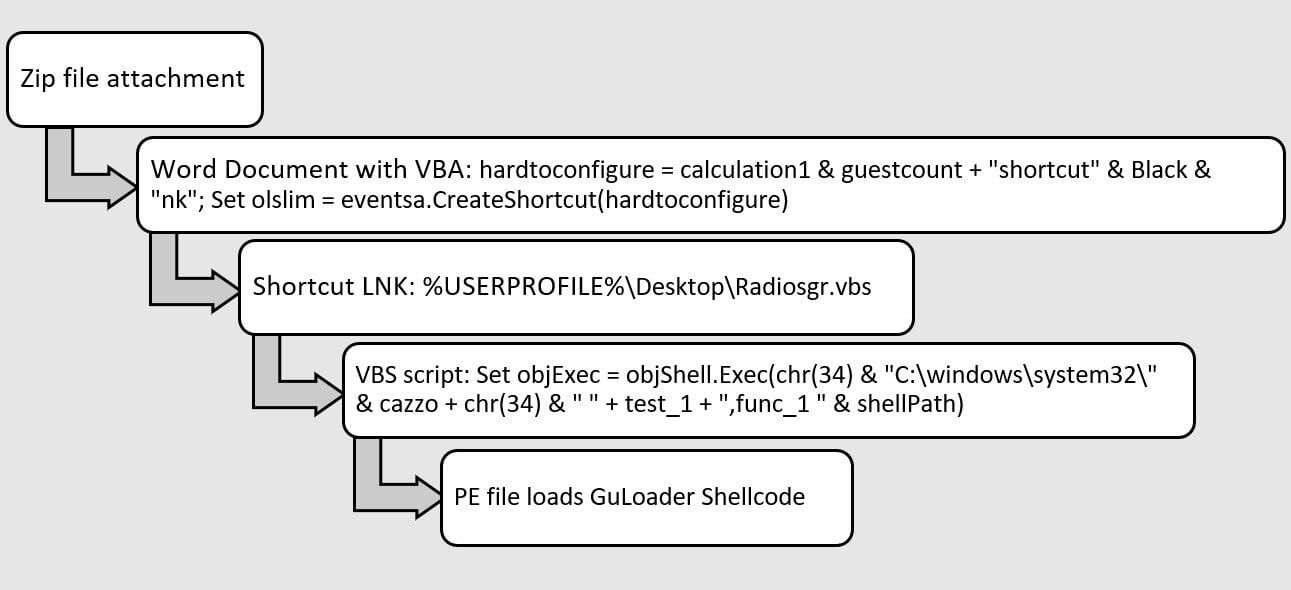
The 2021 attack chain used a ZIP archive containing a macro-laced Word document to drop an executable that loaded GuLoader, but the new phishing wave uses NSIS files embedded in ZIP or ISO images to activate the infection.
The NSIS scripts used to deliver GuLoader have become more sophisticated over the course of 2022, incorporating additional layers of obfuscation, encryption to hide the shellcode and some rude italian words:
This shift is part of a wider trend in the threat landscape, which has seen an increase in alternative malware delivery methods in response to Microsoft’s blocking of macros in Office files downloaded from the internet.
Indicator of Compromises
| SHA256/URL |
|---|
| bd8d50eacc2cb7c6759fa5a62791e8d0 |
| bffd0312e6151472c32be6dea6897b50 |
| aa074c005a4b2e89dedd45bd9d869881 |
| c691bc9cb2682c023351aa7460242eb9 |
| d31f6ec6a53b1a2659d4697b72900dac |
| b53d5a3078e3d1cae1cf8f150987eb7f |
| 22b82f46f0ff7c7a1b375aa84867d277 |
| a5bb4f5bacfabb9c81035fec65a84012 |
| f5e9499818bb35be1d5b670b833216bf |
| 703254254bf23f72b26f54a936cda496 |
| ff091158eec27558905a598dee86c043 |
| 1349db7fd7aaa4a1547cd4381cd7a9b1 |
| https[:]//staninnovationgroupllc[.]com/MYFORMBOOK_eyHVNu169 [.] bin |
| https[:]//drive[.]google[.]com/uc?export=download&id=1ffapdpLWKae2MES2ltCw9RdNejEAZDAQ |
| http[:]//91[.]245[.]255[.]55/java_agent_sZOCrs225 [.] bin |
| http[:]//37[.]120[.]222[.]192/texas_TYBnb22 [.] bin |
| http[:]//linkedindianer[.]com/infoo_UXXITSZ73 [.] bin |
| http[:]//193[.]239[.]86[.]180/build_CMxTGk211 [.] bin |
| http[:]//www[.]aortistf[.]tk/MAKS_rOOOVChP166 [.] bin |
| http[:]//jmariecompany[.]com/kOrg_sIhYtzsF95 [.] bin |
| https[:]//drive[.]google[.]com/uc?export=download&id=1ansa1ONnGoAMkTEB_Wbp1HpGzRPmLHCq |
| http[:]//posadalaprotegida[.]com[.]ar/EbiCBZqpSxRr192 [.] msi |
| https[:]//drive[.]google[.]com/uc?export=download&id=1YScc0lvOAwwaCDu5uuYbn6tWSsZGxlEM |
| https[:]//drive[.]google[.]com/uc?export=download&id=1bR29icPd_54Rzhuz9C80B1EpULuWDlVt |
| http[:]//146[.]70[.]79[.]13/GPUARDJZecPp13 [.] smi |
| http[:]//45[.]137[.]117[.]184/hvntfVSKcCQt84 [.] dsp |