Russian threat group steal screenshots from victims devices
A Russian threat group, dubbed TA866 by Proofpoint, is suspected of using a new technique to steal sensitive information. The group has been taking screenshots of infected devices and uploading them to a remote server.
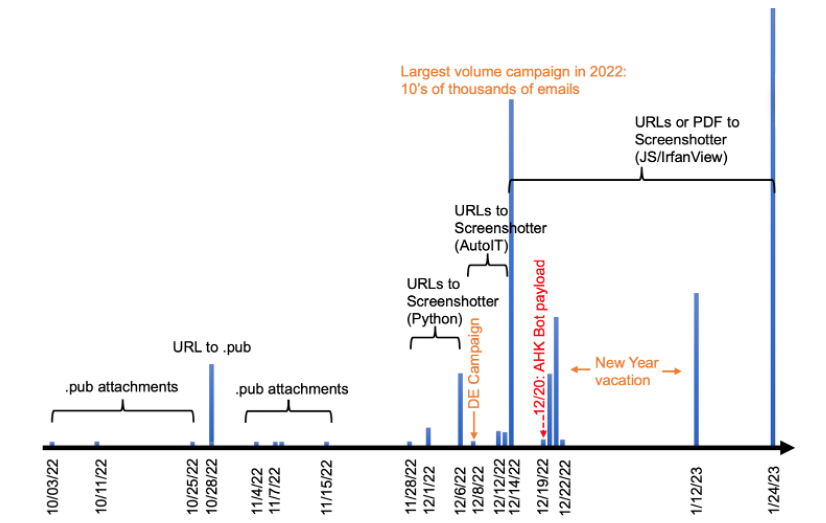
The use of screenshots is becoming increasingly common among threat actors as it is an easy and effective way to gather information.
This technique allows cybercriminals to gather sensitive information without directly exfiltrating the data, targeting individuals and organisations in the financial, legal and political sectors.
The group’s tactics, techniques and procedures (TTPs) have been observed in several recent campaigns: the majority of the activities was observed in October 2022, but there have been multiple clusters of activity identified since 2019.
Indicator of Compromise
| Domain/SHA256/URL |
|---|
| southfirstarea[.]com |
| peak-pjv[.]com |
| otameyshan[.]com |
| thebtcrevolution[.]com |
| annemarieotey[.]com |
| expresswebstores[.]com |
| styleselect[.]com |
| mikefaw[.]com |
| fgpprlaw[.]com |
| duncan-technologies[.]net |
| black-socks[.]org |
| virtualmediaoffice[.]com |
| samsontech[.]mobi |
| footballmeta[.]com |
| gfcitservice[.]net |
| listfoo[.]org |
| duinvest[.]info |
| shiptrax24[.]com |
| repossessionheadquarters[.]org |
| bluecentury[.]org |
| d934d109f5b446febf6aa6a675e9bcc41fade563e7998788824f56b3cc16d1ed |
| hxxp[:]//79[.]137.198.60/1/ke.msi |
| 29e447a6121dd2b1d1221821bd6c4b0e20c437c62264844e8bcbb9d4be35f013 |
| 292344211976239c99d62be021af2f44840cd42dd4d70ad5097f4265b9d1ce01 |
| hxxp[:]//109[.]107.173.72/%serial% |
| 02049ab62c530a25f145c0a5c48e3932fa7412a037036a96d7198cc57cef1f40 |
| d0a4cd67f952498ad99d78bc081c98afbef92e5508daf723007533f000174a98 |
| 6e53a93fc2968d90891db6059bac49e975c09546e19a54f1f93fb01a21318fdc |
| 322dccd18b5564ea000117e90dafc1b4bc30d256fe93b7cfd0d1bdf9870e0da6 |
| hxxp[:]//109[.]107.173.72/screenshot/%serial% |
| 1f6de5072cc17065c284b21acf4d34b4506f86268395c807b8d4ab3d455b036b |
| 3242e0a736ef8ac90430a9f272ff30a81e2afc146fcb84a25c6e56e8192791e4 |
| 3db3f919cad26ca155adf8c5d9cab3e358d51604b51b31b53d568e7bcf5301e2 |
| hxxp[:]//89[.]208.105.255/%serial%-du2 |
| hxxp[:]//89[.]208.105.255/%serial% |
| hxxp[:]//89[.]208.105.255/download?path=e |
| moosdies[.]top |