How to detect Sliver C2 framework activities
Sliver is an open source cross-platform adversary emulation/red team framework, developed for penetration testing purposes but, as other similar softwares like Cobalt Strike, is also used by cybercriminals to malicious activities. It is becoming increasingly popular among cybercrime gangs due to its versatility and flexibility.
Features
- Dynamic code generation
- Compile-time obfuscation
- Multiplayer-mode
- Staged and Stageless payloads
- Procedurally generated C2 over HTTP(S)
- DNS canary blue team detection
- Secure C2 over mTLS, WireGuard, HTTP(S), and DNS
- Fully scriptable using JavaScript/TypeScript or Python
- Windows process migration, process injection, user token manipulation, etc.
- Let’s Encrypt integration
- In-memory .NET assembly execution
- COFF/BOF in-memory loader
- TCP and named pipe pivots
There are some groups that are known to be using the Sliver framework, including Advanced Persistent Threat (APT) groups and ransomware gangs.
These groups use Sliver to launch highly sophisticated attacks, such as the Ryuk ransomware attack and the SolarWinds supply chain attack.
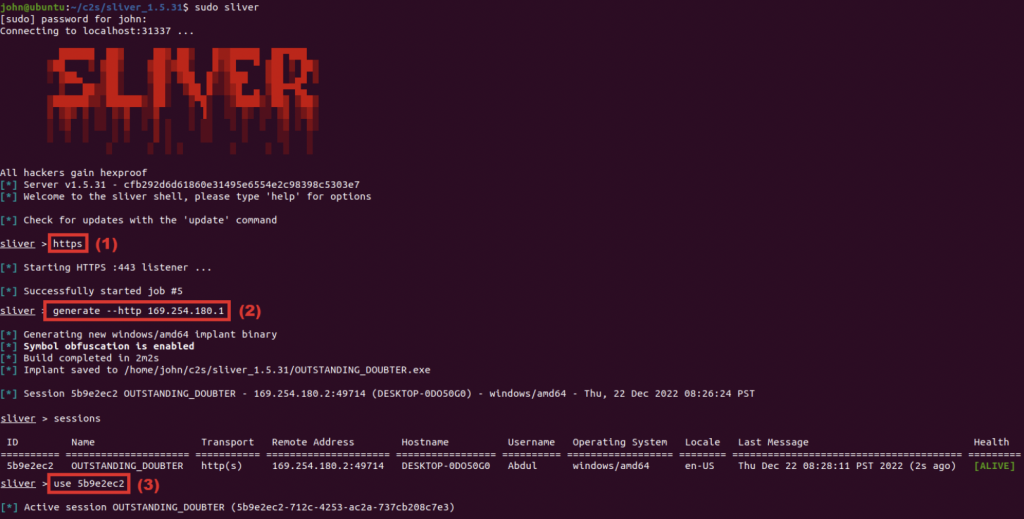
According to this article by VMware, in order to detect Sliver related activities, is mandatory for organizations to implement a multi-layered approach to security, which should include the use of endpoint detection and response (EDR) tools, network traffic analysis, and file system monitoring.
The article highlights three methods to detect Sliver:
Network Traffic Analysis
This method involves monitoring network traffic to detect Sliver traffic patterns and signatures. For example, Sliver C2 traffic is encrypted using a custom encryption algorithm, which can be detected by monitoring network traffic. Additionally, organizations can monitor for specific IP addresses, domain names, and ports used by C&C traffic. Another example could be the following Yara rule, developed by Daniel Roberson:
rule sliver_client : c2 implant
{
meta:
description = "Bishop Fox's Sliver C2 Implant"
author = "Daniel Roberson"
url = "https://github.com/BishopFox/sliver"
strings:
$s1 = "github.com/bishopfox/sliver/client"
condition:
all of them and filesize < 50MB
}
rule sliver_server : c2
{
meta:
description = "Bishop Fox's Sliver C2 Server"
author = "Daniel Roberson"
url = "https://github.com/BishopFox/sliver"
strings:
$s1 = "RunSliver"
condition:
all of them and filesize > 50MB
}
File System Monitoring
this method involves monitoring the file system for Sliver’s executable files related Indicators of Compromise (IoCs).
Organizations can detect the presence of Sliver C2 by monitoring for these files, as well as changes to specific system files such as the Windows registry.
An update list of Indicators of Compromise (IoC), for example the following provided by Malware Bazaar, could be useful for this method:
| First seen | SHA256 |
|---|---|
| 2023-01-05 19:38:07 | 3221de492e436a79655b4a82b72830a28de3aa417300fdf06e0b28202053ff3e |
| 2023-01-05 19:37:00 | 1846c1db07d4f9a3a86605e38c0be5da38074b91cfafa1a72bccc693b06346e4 |
| 2022-12-16 19:20:46 | f63993a7e4dc3e4242509482ca4d9ee1cbd4c00d219503ecf5d139d763a42f35 |
| 2022-07-18 08:00:49 | 78eb647f3d2aae5c52fcdc46ac1b27fb5a388ad39abbe614c0cfc902d223ccd6 |
| 2022-07-18 08:00:44 | f13deec28f6f6d3f4f555f5a2db48cd8a541be52c331ccfccba929e4dfd6bc7a |
| 2022-07-18 08:00:39 | fa647a34b88c5409a58d2f2568147fa03112eb8bfa34bccd801830446213d7c4 |
| 2022-07-18 08:00:32 | 5568131f894caf1217f4cbda3dd40c1f39e680ce7727ed4a767cd1986e7805f0 |
| 2022-07-18 08:00:26 | 5c973707940097122ec97fcb73e7b14f054c11c7e1dd958efe933ae3c6a78c4e |
Endpoint Detection and Response (EDR) Tools
EDR tools are designed to detect and respond to threats on endpoints , and can detect Sliver activity by monitoring for specific behaviors, such as the execution of malicious files or the use of specific network connections.
For example, the following list of network indicators, provided by AlienVault, could be useful:
| Indicator | Type |
|---|---|
| 43[.]128.62.42 | IPv4 |
| 45[.]144.3.216 | IPv4 |
| hxxp://43.128.62.42/acl.exe | URL |
| hxxp://45.144.3.216/powercat.ps1 | URL |
| 5[.]199.173.103 | IPv4 |
| 61[.]155.8.2 | IPv4 |
| hxxp://43.128.62.42:8888 | URL |
| hxxp://45.144.3.216/2.ps1 | URL |
| hxxp://45.144.3.216:14356 | URL |
| hxxp://5.199.173.103/7za.exe | URL |
| hxxp://5.199.173.103/syse.bat | URL |
| hxxp://5.199.173.103/t.zip | URL |