Some thoughts on MLOps security
MLOps, which stands for Machine Learning Operations, is a relatively new field that focuses on the integration of machine learning models into the development and deployment processes of software applications.
MLOps can bring significant benefits to organizations, such as improving the accuracy and performance of machine learning models, increasing efficiency, and reducing costs.
However, it also introduces new security challenges that must be addressed to protect sensitive data and ensure the integrity and reliability of machine learning systems.
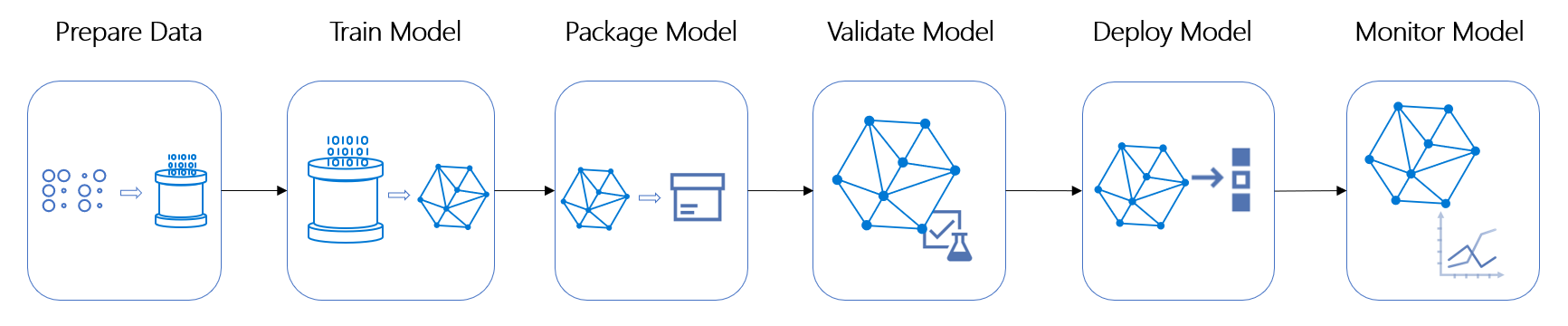
So, in this article, I’d like to discuss about security challenges associated with MLOps, and try to collect practical advice on how to mitigate these risks.
Data security
Data is the lifeblood of machine learning models, and it is essential to keep it secure at all times. Organizations must establish proper access controls to prevent unauthorized access to sensitive data, and ensure that data is encrypted both at rest and in transit. Data should also be stored in secure locations, such as on-premises data centers or cloud storage platforms with robust security controls. According to this article by TrendMicro, a a zero trust model could be the best solution:
This security policy requires the authentication and authorization of all users wanting access to applications or data in a data storage facility. The policy validates users to ensure their devices have the proper privileges and continuously monitors their activity. Identity protection and risk-based adaptive authentication can be used to verify a system or user identity. You can also encrypt data, secure emails, and ascertain the state of endpoints before they connect to the application in the data storage facility.
Model security
Machine learning models are vulnerable to attacks such as adversarial examples, model poisoning, and backdoor attacks. Adversarial examples are specially crafted inputs that can cause a machine learning model to produce incorrect results, while model poisoning involves manipulating the training data to introduce biases or other unwanted behaviors:
Data poisoning is a significant threat to ML models. A slight deviation in the data can make your ML model ineffective. Mainly, attackers aim to manipulate training data to ensure the resultant ML model is vulnerable to attacks. You should avoid sourcing your training data from untrusted datasets while following standard data security detection and mitigation procedures. Poisoned data puts the trustworthiness and confidentiality of your data in question and, ultimately, the ML model.
Backdoor attacks involve inserting a trigger into a model that can be activated by an attacker, leading to unexpected and harmful outputs. To mitigate these risks, it is essential to conduct thorough testing and validation of models and establish monitoring and alerting systems to detect anomalies in model behavior.
Infrastructure security
MLOps requires a complex infrastructure to support the development, training, and deployment of machine learning models. This infrastructure is vulnerable to a range of attacks, including denial of service (DoS) attacks, malicious code injections, and supply chain attacks. To protect the infrastructure, organizations should ensure that all components are properly secured, regularly patch and update software and operating systems, and implement strong access controls and monitoring:
Human error
Mistakes made by developers, data scientists, and other personnel can also pose a significant security risk to MLOps systems. Human error can result in incorrect data labeling, flawed model training, and misconfigurations that leave systems open to attack. To mitigate this risk, organizations must establish clear policies and procedures for MLOps development and operations, provide training and education to personnel, and conduct regular audits and reviews of MLOps systems to identify potential security gaps.
Compliance and regulatory requirements
MLOps systems must comply with a range of regulatory requirements, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS). Failure to comply with these requirements can result in legal penalties and damage to an organization’s reputation. To ensure compliance, organizations should establish clear policies and procedures for data handling, security, and privacy, and conduct regular audits and reviews to identify compliance gaps.