Frebniis: new malware targets Microsoft IIS
Recent research by security firm Symantec has uncovered a new strain of malware called FrebniiS that is specifically designed to target servers running Microsoft Internet Information Services (IIS) software.
This malware is designed to steal sensitive data from the servers, such as payment information and login credentials.
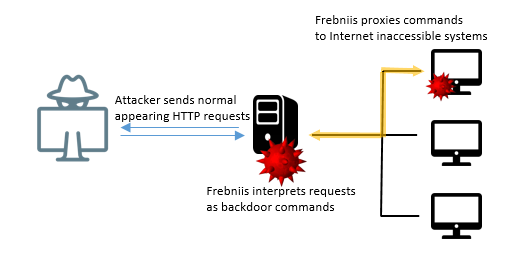
FrebniiS targets IIS servers by exploiting a known vulnerability in the software. Once the malware has gained access to the server, it uses a variety of obfuscation techniques to avoid detection. These techniques include encrypting the malware payload and using random filenames to make detection more difficult:
The technique used by Frebniis involves injecting malicious code into the memory of a DLL file (iisfreb.dll) related to an IIS feature used to troubleshoot and analyze failed web page requests. This allows the malware to stealthily monitor all HTTP requests and recognize specially formatted HTTP requests sent by the attacker, allowing for remote code execution. In order to use this technique, an attacker needs to gain access to the Windows system running the IIS server by some other means. In this particular case, it is unclear how this access was achieved.
FrebniiS is believed to have been created by a Russian-speaking group.
The malware has been used in several attacks against companies and organisations, and experts expect it to be used in more attacks in the future.
Indicator of Compromise
| SHA256 |
|---|
| 6464f9a5da26aa53fb2221255e908fd4da8edf0633f94051beee74a14b9b001c |
| b81c177c440e84635f22dc97b0411de93a24a983a41af676ffbbb4439487aaef |