GoBruteforcer: new malware targets web servers
Researchers at Palo Alto Networks Unit 42 have discovered a new malware called GoBruteforcer, written in Golang and targeting web servers running phpMyAdmin, MySQL, FTP and Postgres.
The malware scans Classless Inter-Domain Routing (CIDR) blocks and brute-force passwords using a list of credentials hardcoded into the binary. If successful, the malware deploys an Internet Relay Chat (IRC) bot on the victim server to establish communication with an actor-controlled server.
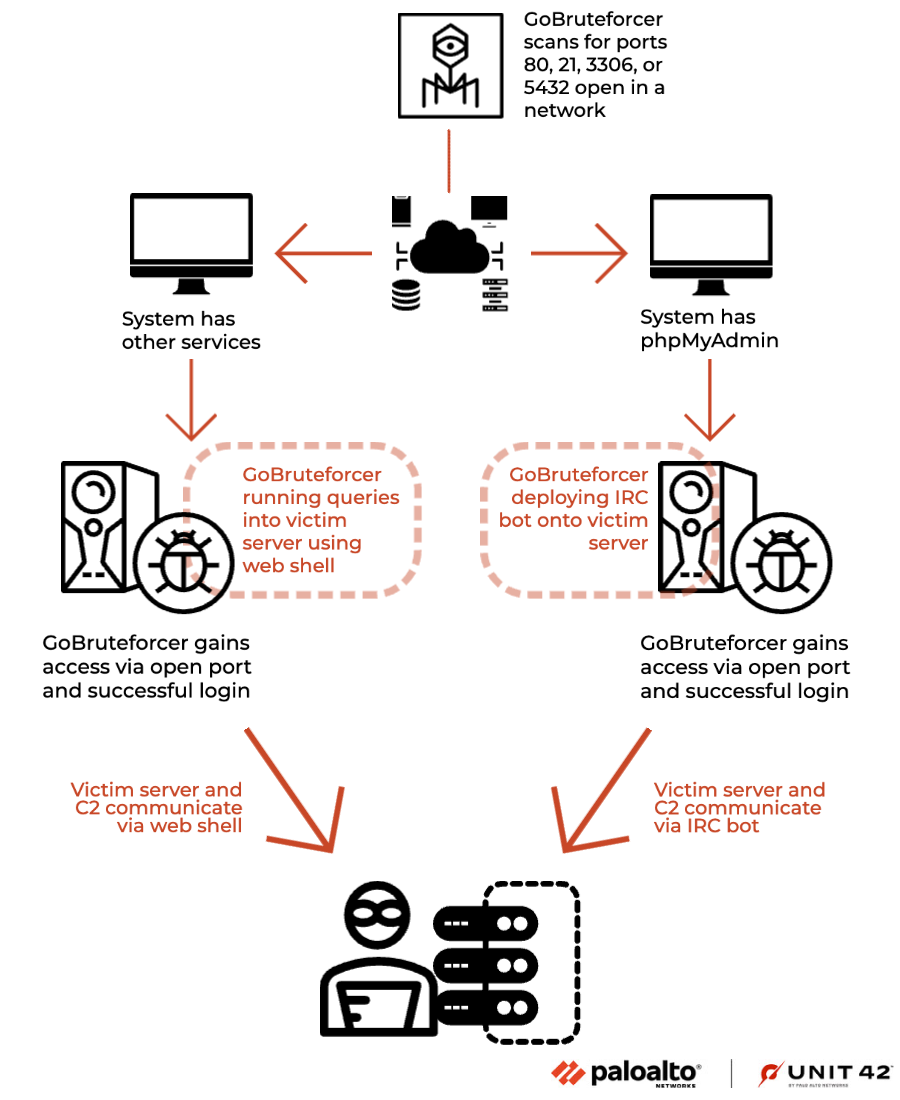
GoBruteforcer also uses any PHP web shell already installed on the victim server to gather further details about the target network. The initial intrusion vector used to deliver the malware is undetermined, and artefacts suggest ongoing development efforts to evade detection.
Indicator of Compromise
| SHA/IP/URL |
|---|
| de7994277a81cf48f575f7245ec782c82452bb928a55c7fae11c2702cc308b8b |
| 602129f00bb002f07db07affa78d46f67bd0b2c8fb0867ea2da5fc3e73dd2665 |
| acc705210814ff5156957c028a8d6544deaca0555156504087fdc61f015d6834 |
| 426b573363277554c7c8a04da524ddbf57c5ff570ea23017bdc25d0c7fd80218 |
| 726ccd223a1cfb60fc6c3b48ea3dbf057da918efac5acf620cd026ee38fb0044 |
| 526767fbb26c911601371745d603885b75deabcc18261ed2d5a509d58f95d28e |
| dd3555025957cd51cd048d920027a0ff2d5501bc85792529217d54086e9351c2 |
| df7dc0fe7e90a2414ac188c55d06ad3882cfc7394869c9ffa549fb1ddb304919 |
| ebe11121aafdac5d8f2eecba710ba85efa31617a5eb825ba2e89e23379b26b84 |
| 5548935e7c6cf3b38240a0579cac36906e9883a1ec5e85335609e9e2062588c5 |
| 5627b138bc857081d2251edd7eb3b68cbd58dfff2f51b7cd34c893fffff2cfab |
| 5c1d3fb43e9e35b835e62e05a7b97ed66ab132eab35bfc18ce543e8f58ccf5e2 |
| 7c27ac0daba19de227fcc467abfcdefa99426c768a3601b1b181e9741717665b |
| 5.253[.]84[.]159/x |
| fi[.]warmachine[.]su |