Dero cryptocurrency mining campaign discovered by CrowdStrike
CrowdStrike has discovered a cryptojacking campaign targeting Kubernetes infrastructure, believed to be the first Dero cryptojacking operation.
Dero is a private, decentralised application platform that offers enhanced privacy and anonymity compared to other cryptocurrencies.
The attack targets Kubernetes clusters exposed to the internet with anonymous access enabled on Kubernetes API: the attackers use a DaemonSet to deploy a malicious pod on each node of the cluster to perform the cryptojacking operation.
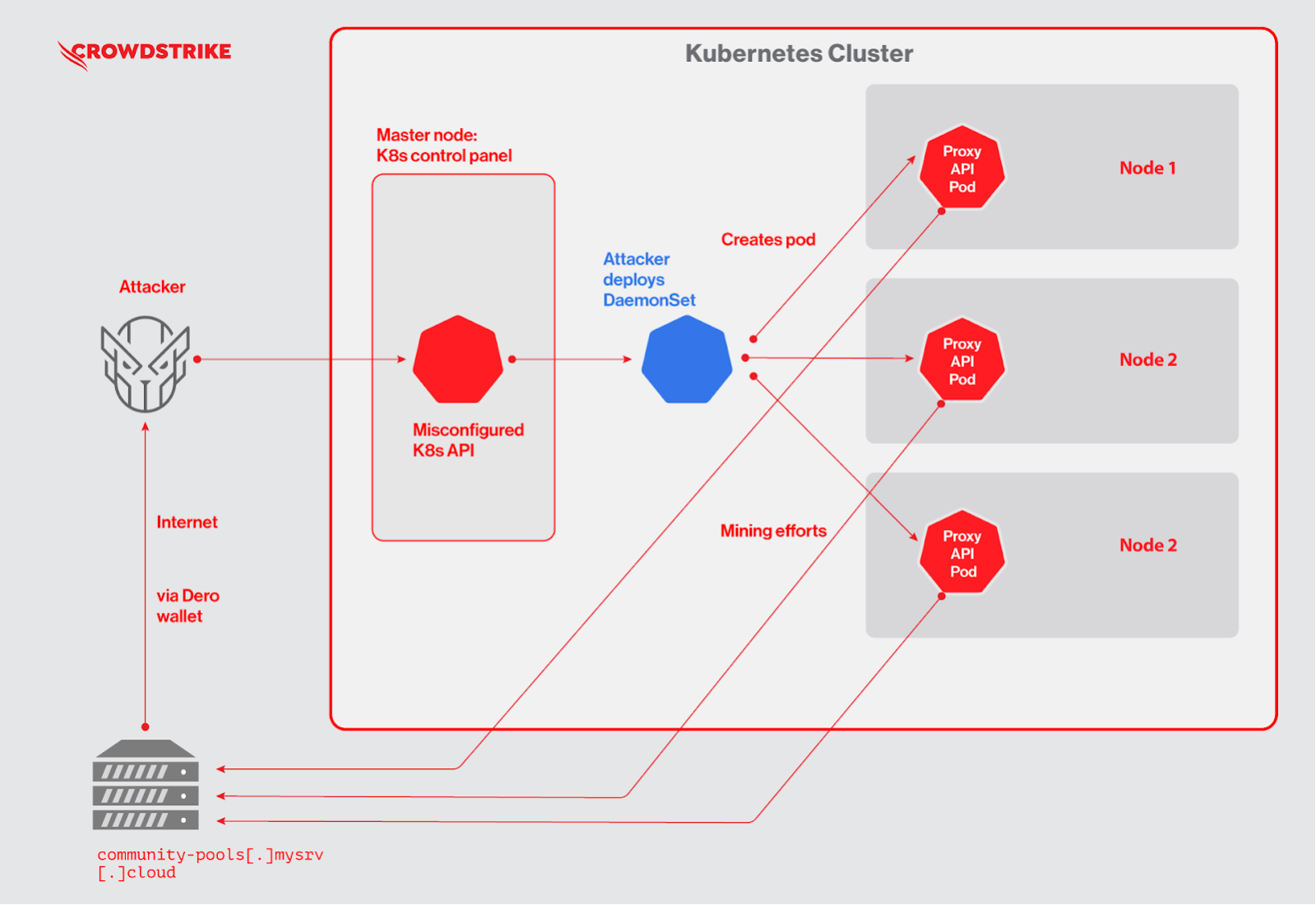
According to the report, a competing group running a Monero-mining campaign is trying to target exposed Kubernetes clusters by trying to remove the “proxy-api” DaemonSet that is connected to the Dero campaign:
At the same time, CrowdStrike observed another Monero campaign, which is modified and is aware of the Dero campaign and targeting the same attack surface but using a more sophisticated approach. Both campaigns are trying to find undiscovered Kubernetes attack surfaces and are battling it out.