Vulnerability allows restoration of sensitive information on Google Pixel screenshots
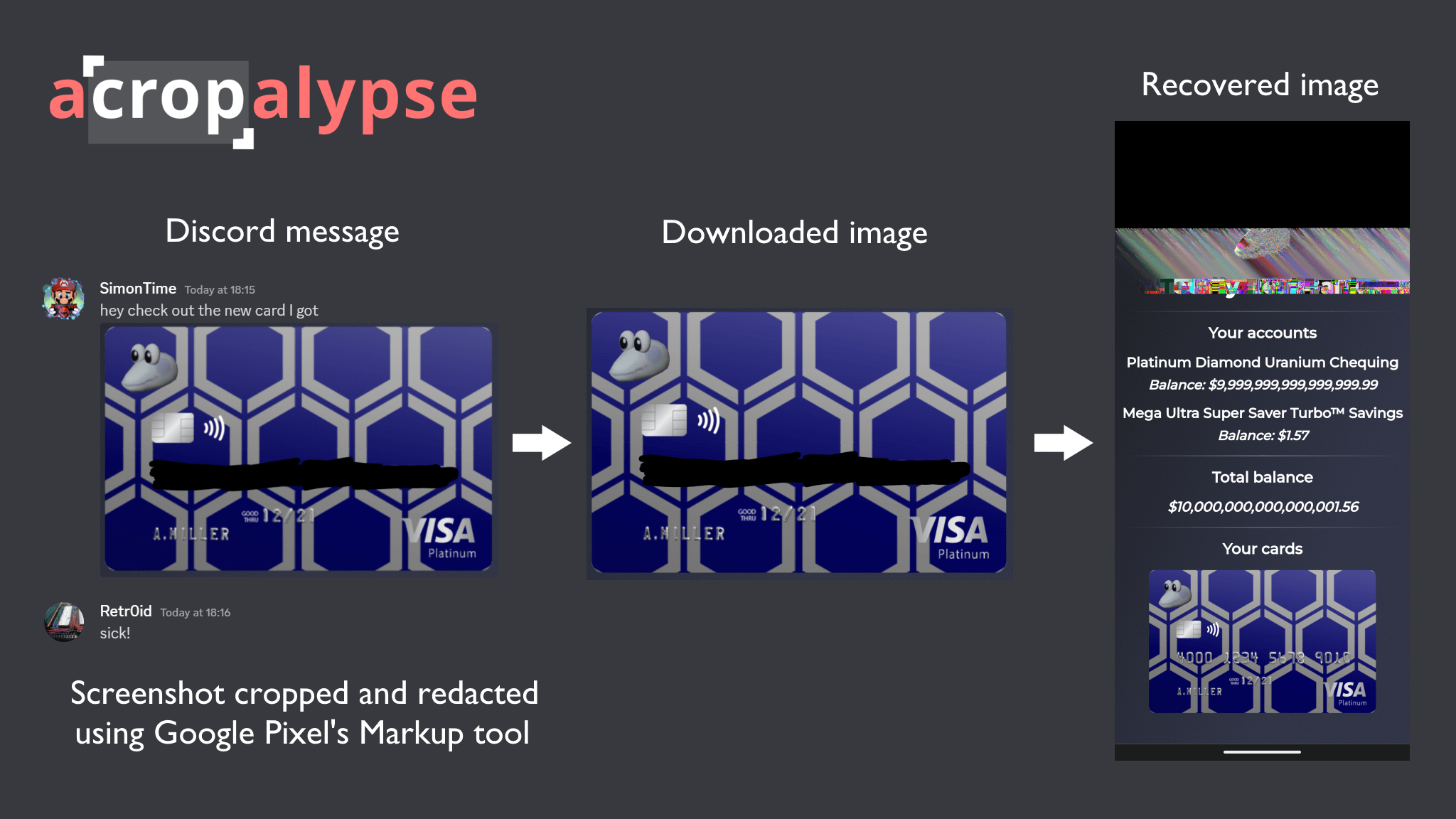
Security researchers David Buchanan and Simon Aarons have discovered a serious vulnerability in Google Markup, the screenshot editing tool available on Pixel devices. The bug, dubbed “aCropalypse”, allows certain parts of the image to be restored, potentially exposing sensitive information.
The vulnerability, identified as CVE-2023-21036, was introduced about five years ago when Google included the tool in Android 9 Pie. Markup allows users to edit PNG screenshots by cropping or removing personal information, such as passwords, credit card numbers or phone numbers, before sharing the image on social media or through messaging services.
Buchanan and Aarons discovered that the edited screenshot created with markup is saved in the same location as the original image. As a result, if the modified file is smaller, the last part of the original file remains intact, potentially exposing sensitive information.
By using different decompression algorithms, a malicious actor could exploit the vulnerability to recover sensitive information. Users can check if their screenshots are vulnerable by uploading them to this website.
The vulnerability was reported in January and Google issued a patch for Pixel 4a, 5a, 7 and 7 Pro earlier this month. Some platforms automatically process uploaded images by removing the last part of the file, making them immune to the problem.
Twitter is an example of such a platform, while Discord began performing the same operation on 17 January, making it impossible to exploit the vulnerability on earlier screenshots.