TOR Browser installers used to spread cryptocurrency theft malware
Since September 2022, trojanised installers for the TOR browser have been used to distribute Clipper malware, which steals cryptocurrency from users in Russia and Eastern Europe.
The malware scans clipboard contents for cryptocurrency wallet addresses and replaces them with addresses from a hardcoded list. According to a research published by cybersecurity firm Kaspersky, the malware has been distributed via unknown third-party sources or torrent downloads, as the Tor Project website is blocked in Russia.
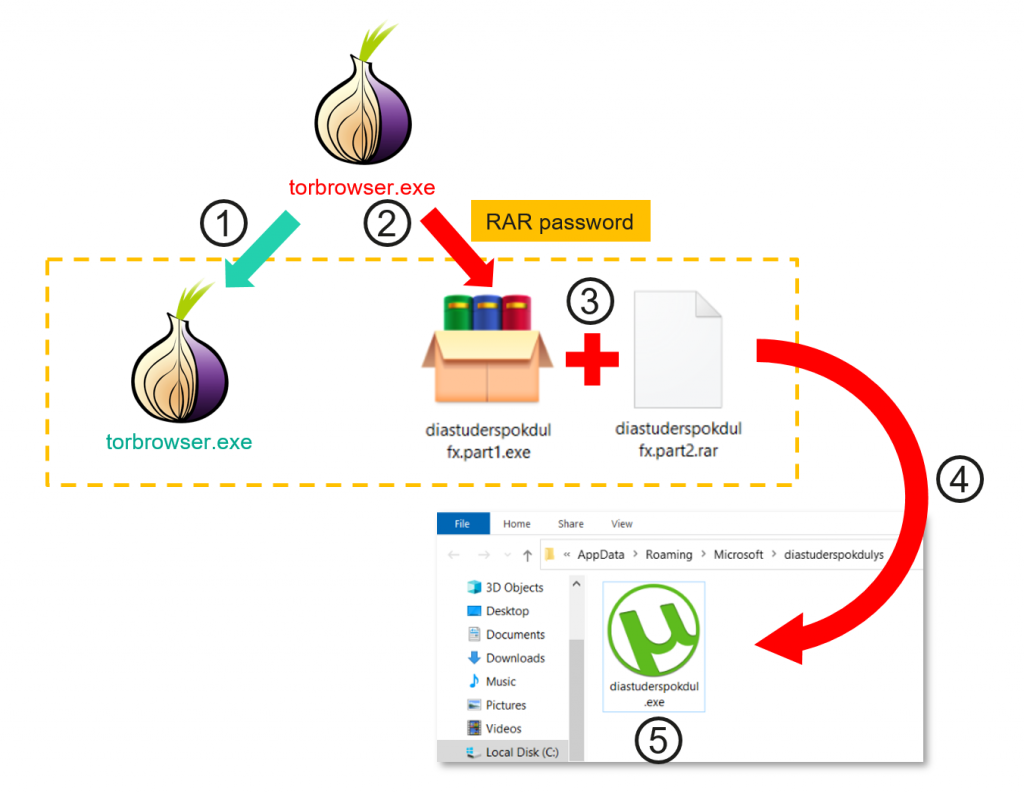
The Clipper malware has long evaded detection due to its silent presence, and the scheme has generated nearly $400,000 in illegal profits for its operators.
The campaign may be more widespread, with the threat actors possibly using other installers and delivery methods.
Indicator of compromise
| HASH |
|---|
| 0251fd9c0cd98eb9d35768bb82b57590 |
| 036b054c9b4f4ab33da63865d69426ff |
| 037c5bacac12ac4fec07652e25cd5f07 |
| 0533fc0c282dd534eb8e32c3ef07fba4 |
| 05cedc35de2c003f2b76fe38fa62faa5 |
| 0a14b25bff0758cdf7472ac3ac7e21a3 |
| 0b2ca1c5439fcac80cb7dd70895f41a6 |
| 0c4144a9403419f7b04f20be0a53d558 |
| 0d09d13cd019cbebf0d8bfff22bf6185 |
| 0d571a2c4ae69672a9692275e325b943 |
| a7961c947cf360bbca2517ea4c80ee11 |
| 0be06631151bbe6528e4e2ad21452a17 |
| a2b8c62fe1b2191485439dd2c2d9a7b5 |
| 53d35403fa4aa184d77a4e5d6f1eb060 |
| ad9460e0a58f0c5638a23bb2a78d5ad7 |
| cbb6f4a740078213abc45c27a2ab9d1c |
| eaf40e175c15c9c9ab3e170859bdef64 |
| 89c86c391bf3275790b465232c37ddf5 |
| 1ce04300e880fd12260be4d10705c34f |
| c137495da5456ec0689bbbcca1f9855e |