Cybercriminals use SFX archives to install backdoors
CrowdStrike researchers have discovered that SFX archives used to share compressed files with those who do not have WinRAR on their computers are being exploited to hide infected files capable of installing backdoors that bypass operating system security measures.
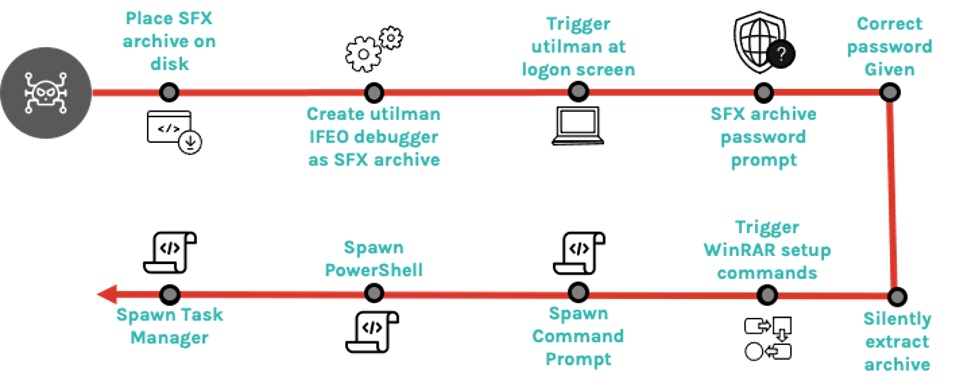
Cybercriminals use WinRAR SFX archives to install a backdoor after gaining access to Windows with stolen credentials by adding a key to the registry that uses the Utilman application to run the SFX file before login.
The malware runs in the background and users see a ‘bait’ document on their screens.
A Trustwave blog post published in October 2022 details how the notorious Emotet botnet was sending out an SFX archive that, once opened by a user, would automatically extract a second password-protected SFX archive, enter the password, and execute its content without further user input. The archive also displayed a decoy file to avoid raising suspicions.
The researchers suggest that users should examine the contents of an SFX archive and identify any dangerous commands before running the file, as many anti-virus programs do not detect this type of threat.
Indicators of compromise
| SHA1 |
|---|
| FF86161334B70BCC2A5D638AD2AB2BF3980DC457 |
| DB7A08AB199F7F341F90D05A6B09846C6D43F8CB |
| 4C0F487D60FC4F1ADB29128EC9FD044C10E8653F |
| 9A5021D6679E2E8ECF900D6B5FF2CDA9715E83DB |
| 0B9381FFC9AE3A7749484D0AD788E91452DAE86B |
| 541BF4E5FA5FBEC25374BEF131C59070DA9D3C4A |
| B4E93ED6ED7038CDD70F4791B73EED849F49275B |
| C29C5382074F64176FE3904D24492A4DAC45C123 |
| 925E4A825C139DF9535A4D4649A4CF64656E3194 |
| 48741C6E3E736FD5083F0DEF8E3741CE4E60B944 |
| 88444E90913017BA77CC06FECCA3E659840633C6 |
| CF00D27AF07A40613A7932CD3090D89A8C6B0569 |
| 206ED91982F2011EC20B76CB07AA7BD48E6F81CC |
| E638A4040AE2553410CE77A88968CD7321F55063 |
| E638A4040AE2553410CE77A88968CD7321F55063 |
| D9A78F491AF45BB3DC02E764217D89DD95F4F17C |
| A602E13CCE53CE9D589D9C6386058204BD3CE978 |
| CC63815B9B77FCDD7E3EFAAB3664CA5DB15328AA |
| 5F0C88D8BE30996E3D623E54F49A9E00ADEF3A2E |
| 325E84243E2E901C3CAAEAC533D8931E5C15F043 |
| F625A44582E4C790F3A90E5A7B896AA660166A60 |
| 1118A8A12CD2D59A32A8B6DCFFF279F20351FB9B |
| 78F4166B7611428E076ADCDCCDA34F73DC95CE37 |
| 0A36CAD9F18249D42E05685B00330583C20D0BC3 |