Typhon Reborn malware returns with improved capabilities
According to a report by Cisco Talos, the Typhon Reborn information-stealing malware has returned with an updated version that includes improved capabilities to evade detection and analysis.
The new version, which is being offered for sale on the criminal underground, can harvest and exfiltrate sensitive information and use the Telegram API to send stolen data to attackers.
The malware is capable of hijacking clipboard content, capturing screenshots, logging keystrokes and stealing data from crypto wallets, messaging, FTP, VPN, browser and gaming applications.
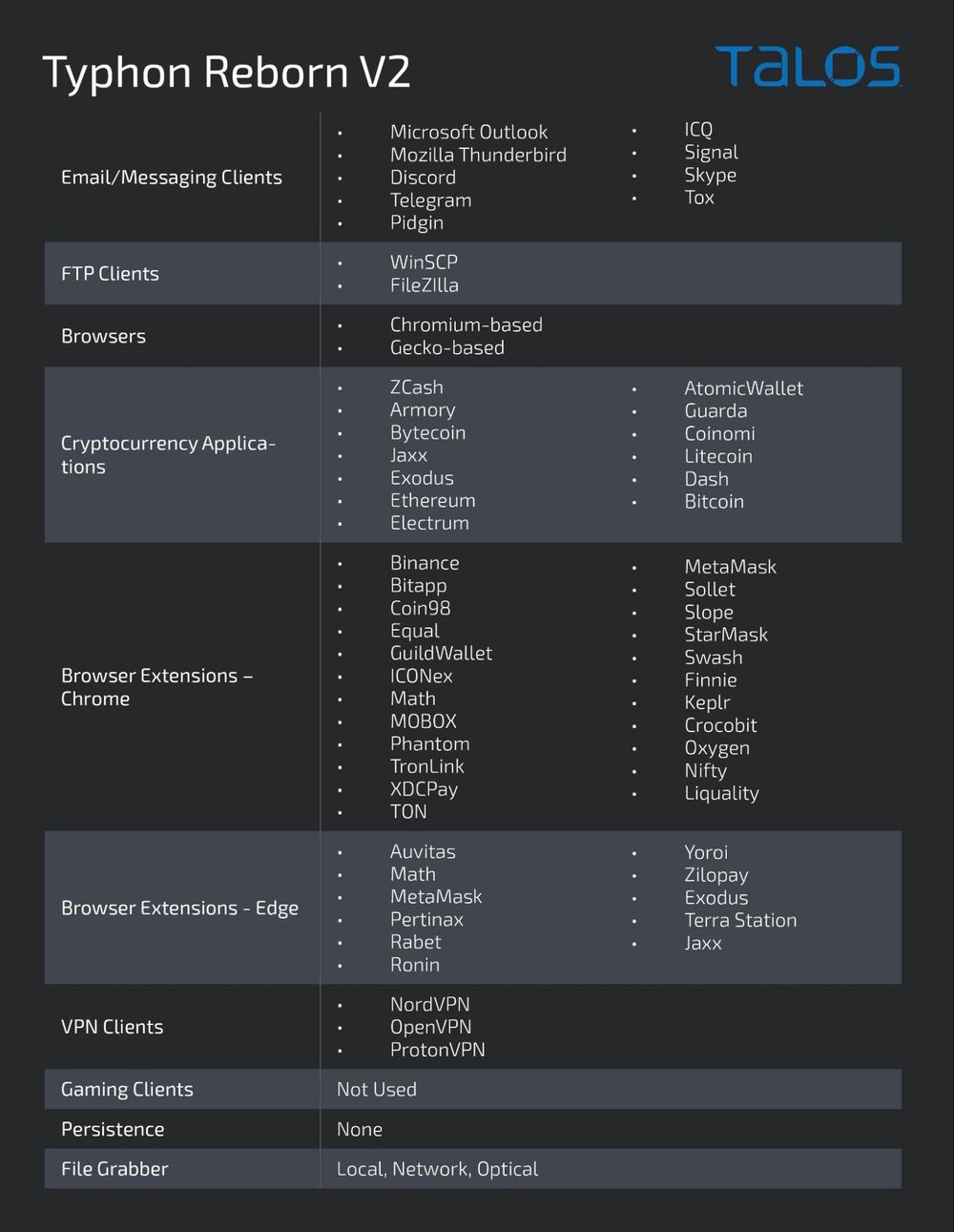
The latest version removes persistence features and terminates itself after exfiltrating data. It also transmits the collected data in a compressed archive over HTTPS using the Telegram API.

The findings come as Cyble disclosed a new Python-based stealer malware named Creal that targets cryptocurrency users via phishing sites mimicking legitimate crypto mining services like Kryptex.

The Creal stealer malware, which is similar to Typhon Reborn, targets cryptocurrency users via phishing sites and exfiltrates data using Discord webhooks and various file hosting and sharing platforms.
The source code for Creal is available on GitHub, allowing other threat actors to modify it.
Indicators of Compromise
| SHA/URL/Domain |
|---|
| 4ee417cbefa1673d088a32df48b8182bdad244541e8dc02faf540b9aa483fdcb |
| f3197e998822bc45cb9f42c8b153c59573aad409da01ac139b7edd8877600511 |
| hxxps[:][//www[.]dropbox][.]com/s/dl/x4vgcaac6hcdgla/kryptex-setup-4.25.7[.]zip |
| kryptex[.]software |
| 369042ac123b4933e6649ea3080152fa569f1717e0b9d560b85f0ca2e49373c2 |
| a12933ab47993f5b6d09bec935163c7f077576a8b7b8362e397fe4f1ce4e791c |
| 1f7556682b8f150a15d0e621257bdb05a150d4b9a0bb55b8d872ce1233919c6e |
| 11062ef5f43e936ecd281c850144f8847ac4aef41d442ab8946636cbbe3aa68a |
| 2d72877dc9c873a127599090b11b2fffaa74adc0cc268fec48d802307715c500 |
| 3ce30c271c6c0ed4665a6b338453946529df80388cba670278c7537982da65b0 |
| 58c3b432a0cb2907079d737b8a6b8d3eb8f66180aedb2ed6daea22a4cec3d2dd |
| 819cda49654a3651c3bb31b2e22cb9e6ae25317caee5277471bc0b1784a27228 |
| 9a84a5f14dc96a056655ac9bde6d197f6be3e99ac6186c2247b5e8285df9c331 |
| b1c11a60c9e3dfd7384348ea7560b47808d04801193d42ecbcce8dd1c280a748 |
| b9a0ab6783fc1e24b947c012dde5dc639629ebf7845b0f1fb4045b721be96565 |
| 50da5db0df4641a8c9c6604c9ef679d2648d6b79c89f7e61d99174d0ec005d52 |
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
|---|---|---|
| Execution | T1204 | User Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Credential Access | T1555 T1539T1528 | Credentials from Password Stores Steal Web Session Cookie Steal Application Access Token |
| Discovery | T1087 T1518 T1057 T1124 T1007 T1614 | Account Discovery Software Discovery Process Discovery System Time Discovery System Service Discovery System Location Discovery |
| Command and Control | T1071 T1102 | Application Layer Protocol Web Service |
| Exfiltration | T1041 | Exfiltration Over C&C Channel |