RTM Locker: private Ransomware-as-a-Service provider with strict rules
A cybercriminal gang called Read The Manual (RTM) Locker has been described in detail by cybersecurity researchers of Trellix .
RTM is a private ransomware-as-a-service (RaaS) provider that conducts opportunistic attacks to generate illicit profits. The group operates through affiliates, all of which must adhere to strict rules in order to remain active or notify the gang of their departure.
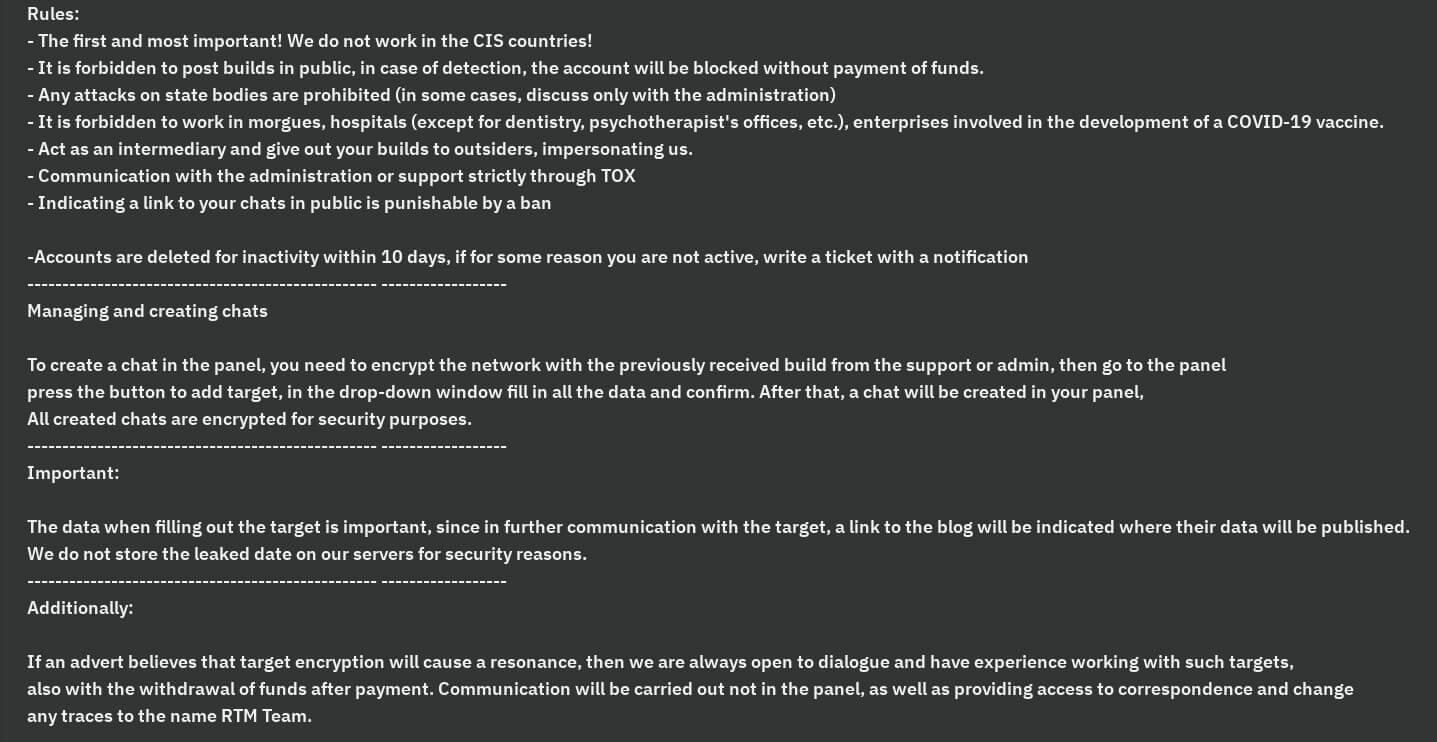
RTM Locker’s malware builds are bound by strict mandates that prohibit affiliates from leaking the samples or risk being banned. The gang’s specific efforts to avoid attracting attention are higher than usually observed compared to other ransomware groups.
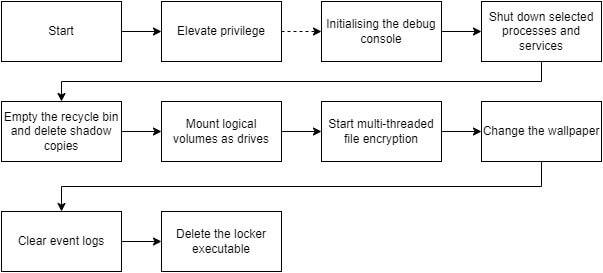
RTM’s tactics suggest that cybercrime groups will continue to adopt new tactics and methods to avoid headlines and fly under the radar of researchers and law enforcement.
MITRE ATT&CK techniques
| Technique ID | Technique | Description |
| T1057 | Process Discovery | Checks which processes are running, and shuts down unwanted processes |
| T1070.1 | Indicator Removal on Host: Clear Windows Event Logs | Clears the event logs once the locker completes its encryption process |
| T1070.4 | Indicator Removal on Host: File Deletion | The locker deletes itself post execution |
| T1106 | Native API | Uses the WinAPI directly |
| T1134.2 | Access Token Manipulation: Create Process with Token | The locker elevates its privilege using the “runas” token |
| T1486 | Data Encrypted for Impact | Encrypts the files on the disk |
| T1489 | Service Stop | Checks which services are running, and stops unwanted on |