Vice Society's new PowerShell script enables automated data theft in ransomware attacks
The Vice Society ransomware gang has developed a new PowerShell script to automate data theft from compromised networks, which is fully automated and uses “living off the land” binaries and scripts to remain undetected.
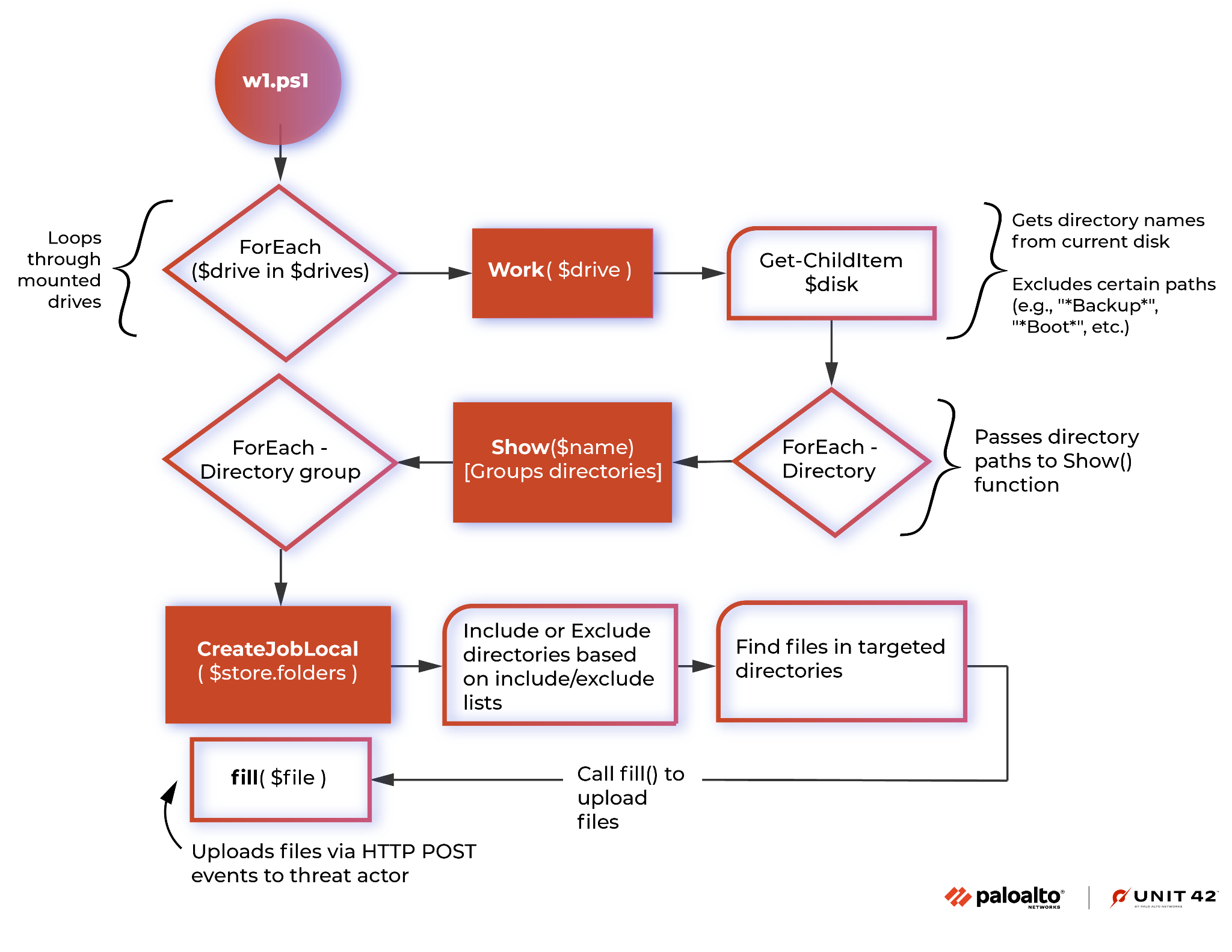
The script uses multiple functions to identify potential directories for exfiltration and eventually exfiltrate data via HTTP POST requests to Vice Society’s servers. The script uses system-native cmdlets to search and exfiltrate data from the infected machine, minimizing its footprint and maintaining a stealthy profile.
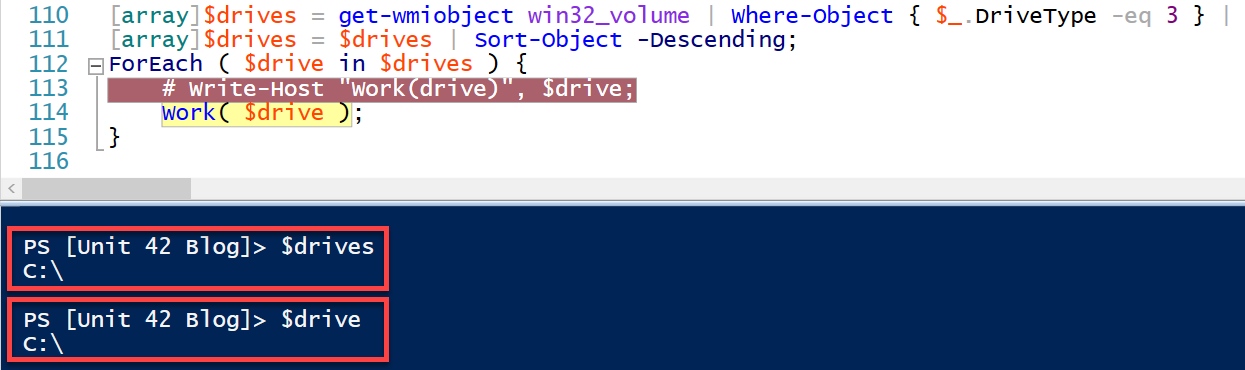
The new data theft tool was discovered by Palo Alto Networks Unit 42 during an incident response in early 2023.This new development makes Vice Society a more formidable threat to organizations worldwide, giving defenders fewer opportunities to detect and stop the attacks.
Indicators of Compromise
Since the script in question was recovered from an Event ID 4104 WEL event, a hash of the true, original file as it may have resided on disk is not available. However, we have included the filename of the script along with the contents recovered from the script in this section.
| Filename |
|---|
| w1.ps1 |