China-linked APT41 group uses Open-Source red teaming tool in cyber attacks
The China-linked APT41 cyberespionage group (also known as HOODOO) used the open-source red teaming tool GC2 in an attack against an unnamed Taiwanese media organization in October 2022, using as payload an open source red teaming tool called “Google Command and Control” (GC2), a Command and Control application that allows an attacker to execute commands on the target machine using Google Sheet and exfiltrates data using Google Drive.
This program has been developed in order to provide a command and control that does not require any particular set up (like: a custom domain, VPS, CDN, …) during Red Teaming activities. Furthermore, the program will interact only with Google’s domains (*.google.com) to make detection more difficult.
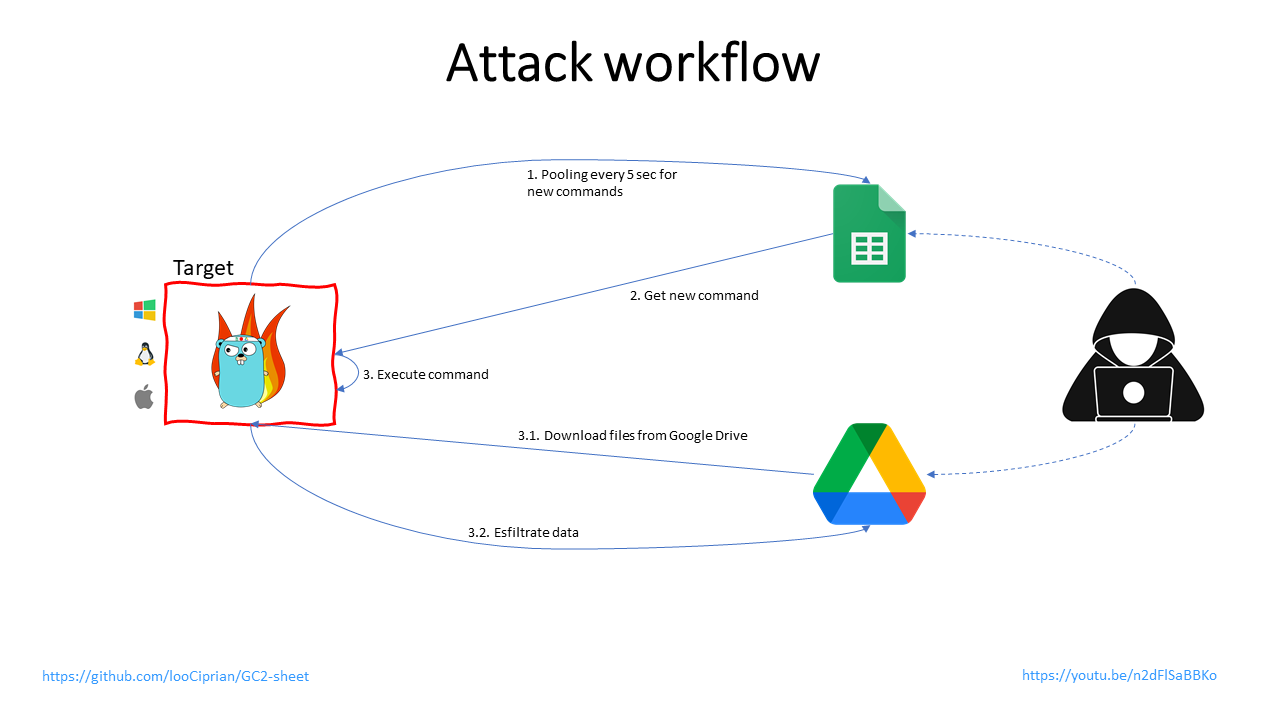
Google’s Threat Analysis Group (TAG) disrupted the campaign, which involved a phishing email that contained links to a password-protected file hosted in Drive, in the April 2023 Threat Horizons Report.
The researchers highlighted that Chinese threat actors are increasingly using publicly available tooling such as GC2 and Cobalt Strike, and the proliferation of tools written in the Go programming language due to its flexibility and modularity.
The report also urges organizations to improve enterprise defenses as cloud services are becoming a privileged target for nation-state actors.