GhostToken: Google Cloud Platform security flaw allows attackers to gain unremovable access to accounts
Google has fixed a security flaw called GhostToken that allowed attackers to backdoor Google Cloud Platform (GCP) users’ accounts using malicious OAuth applications installed from the Google Marketplace or third-party providers.
According to a research by Astrix Security, after being authorized and linked to an OAuth token, attackers could make malicious apps invisible by exploiting the vulnerability, hiding the apps from Google’s application management page.
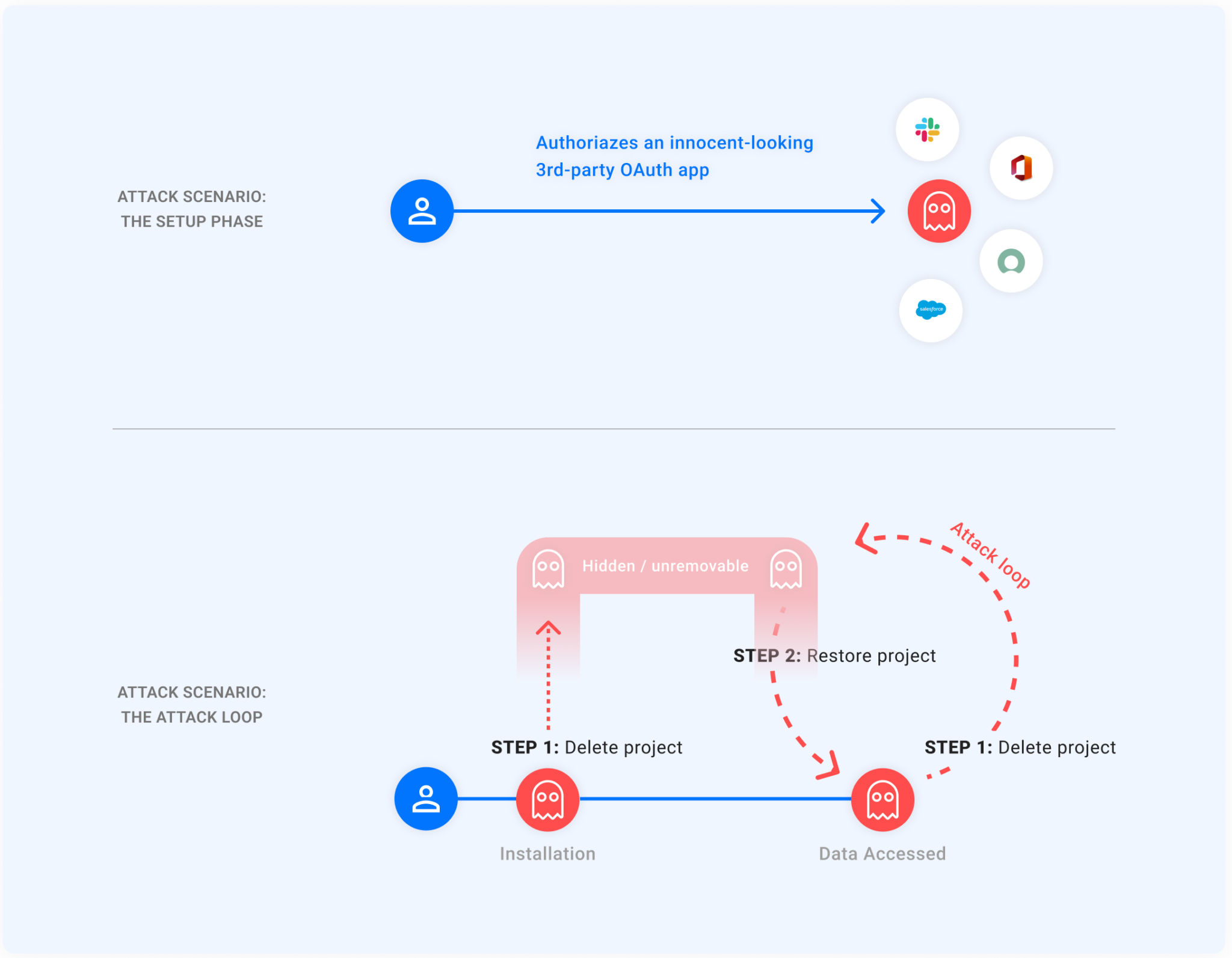
This made the malicious app unremovable from the Google account, allowing attackers to gain permanent and unremovable access to a victim’s Google account.
[…] the only way Google users could remove the access of an OAuth application is through the Apps with access to your account page. This means that while the vulnerability wasn’t patched, all Google users were essentially unable to remove malicious applications exploiting GhostToken.
Google’s patch allows GCP OAuth applications in ‘pending deletion’ states to appear on the ‘Apps with access to your account’ page, allowing users to remove them and protect their accounts from hijack attempts.
Astrix Security advises all Google users to visit their account’s app management page and check all authorized third-party apps, ensuring each of them has only the permissions they require to function.