The Italian Government Email Vulnerability: A Wake-Up Call for Email Server Security Worldwide
The recent investigation by Italian journalists at Fanpage.it has exposed a critical vulnerability that allowed them to clone government email addresses, including that of Prime Minister Giorgia Meloni.
This alarming discovery serves as a stark reminder that even the most sensitive institutional communications remain vulnerable to sophisticated email spoofing attacks. The case demonstrates how inadequate email authentication protocols can compromise national security communications and underscores the urgent need for robust email server security implementations.
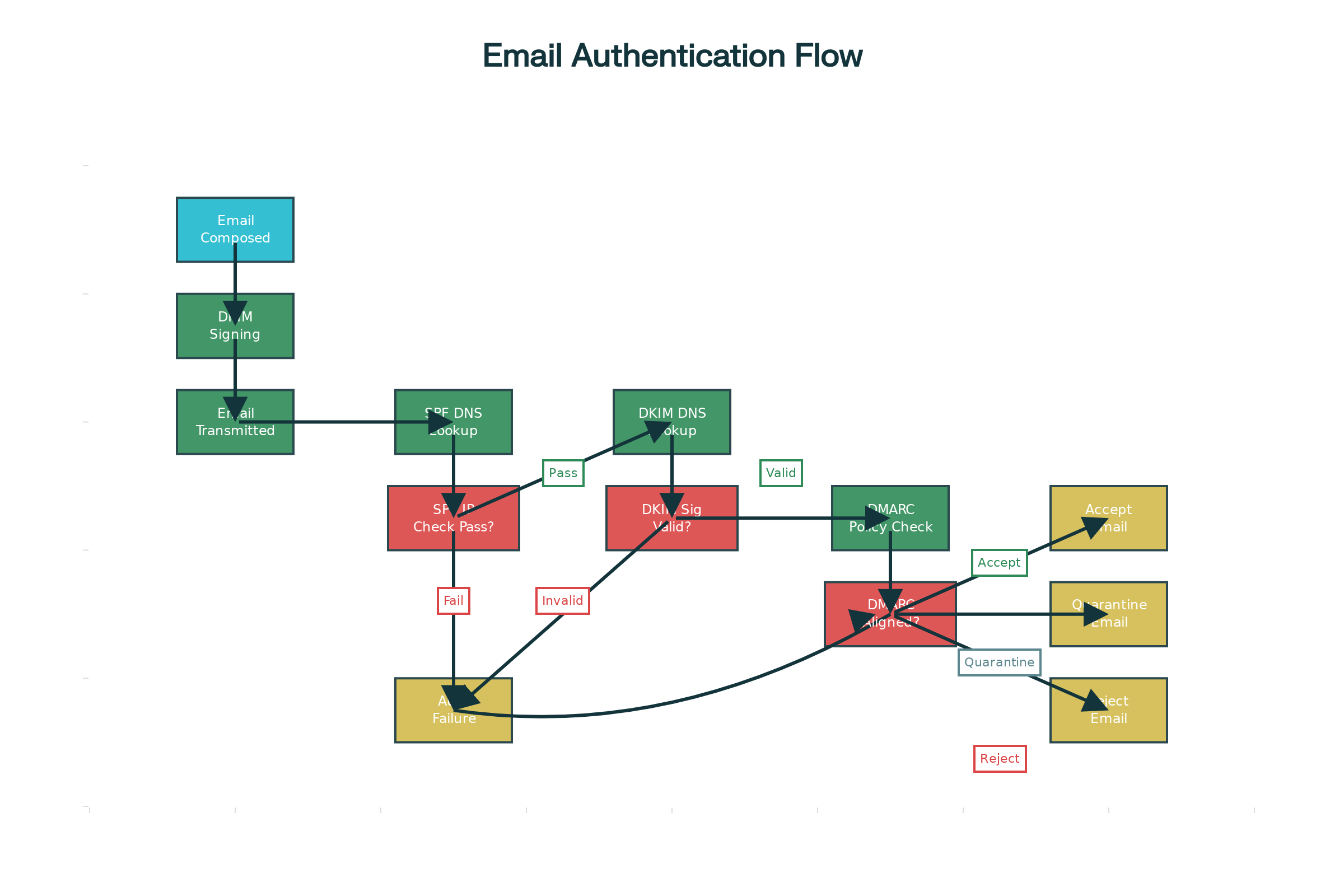
Email Authentication Flow: How SPF, DKIM, and DMARC Work Together
The vulnerability discovered in Italy highlights a fundamental problem affecting government institutions globally: the lack of proper email authentication mechanisms. When essential security protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance) are not correctly implemented or enforced, attackers can exploit these gaps to impersonate legitimate senders. This type of attack, known as email spoofing, allows malicious actors to create emails that appear identical to official communications, bypassing basic security checks and potentially reaching their intended targets.
The Anatomy of Email Spoofing Attacks
Email spoofing represents one of the most insidious threats to organizational security because it exploits the inherent trust users place in familiar sender addresses. The technique involves manipulating email headers to disguise the true source of a message, making it appear as though it originated from a trusted entity. In the Italian case, researchers demonstrated that government domains could be spoofed without compromising actual email accounts, instead leveraging “the absence or misconfiguration of rules that authenticate the sender”. This highlights the critical role of email security in government communications and the evolving nature of phishing techniques.
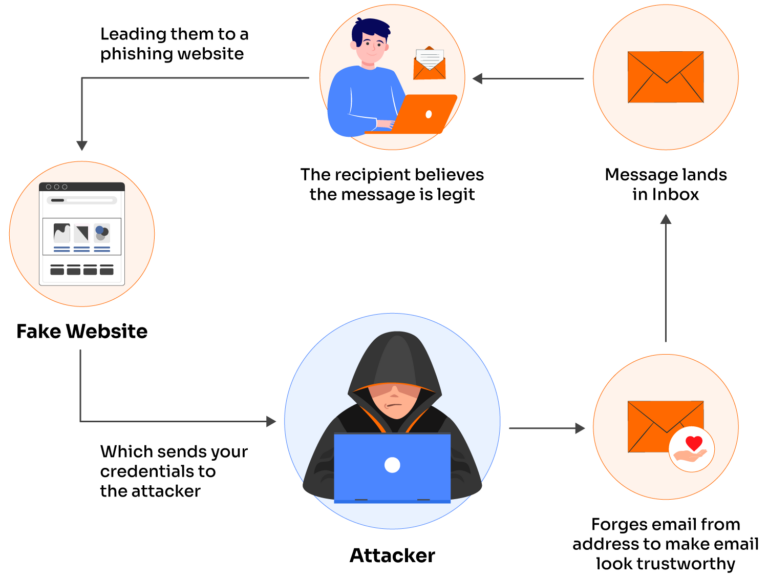
Diagram showing an email spoofing attack where a hacker intercepts and manipulates emails between a legitimate user and a recipient.
The sophistication of modern spoofing attacks has evolved significantly. Attackers now employ multiple techniques including display name spoofing, domain spoofing, and lookalike domain spoofing. Display name spoofing involves changing only the display name while using a suspicious email address, while domain spoofing creates entirely fake domains that closely resemble legitimate ones. The most dangerous variant, complete domain spoofing, allows attackers to send emails that appear to come from the exact domain they’re impersonating, as demonstrated in the Italian government case. These techniques are detailed in comprehensive email authentication guides.
Contemporary email spoofing campaigns are becoming increasingly sophisticated, with threat actors exploiting government website vulnerabilities for phishing campaigns using artificial intelligence to craft more convincing messages. These AI-generated phishing emails avoid traditional red flags like spelling and grammatical errors, making them significantly harder to detect. The combination of perfect spoofing capabilities with AI-enhanced social engineering creates an unprecedented threat landscape that traditional security measures struggle to address, as highlighted in analyses of 2024’s biggest phishing attacks.
Understanding Email Authentication Protocols
The foundation of email security rests on three critical authentication protocols that work together to verify the legitimacy of email communications. Understanding these protocols is essential for implementing effective email security measures that can prevent the type of vulnerability exploited in the Italian case. Comprehensive guides on setting up DMARC, DKIM, and SPF provide the technical foundation needed for robust email authentication.
SPF (Sender Policy Framework)
SPF acts as the first line of defense by specifying which mail servers are authorized to send emails on behalf of a particular domain. When an email is received, the recipient’s server checks the sender’s IP address against the SPF record published in the domain’s DNS settings. If the IP address matches one of the authorized servers, the email passes SPF validation. The Italian investigation revealed that many government domains lacked properly configured SPF records, allowing unauthorized servers to send emails claiming to originate from official government addresses.
Implementing SPF requires careful planning and regular maintenance. Organizations must identify all legitimate email-sending services, including marketing platforms, support systems, and third-party services that send emails on their behalf. The SPF record typically begins with “v=spf1” and includes approved IP addresses and domains using mechanisms like “include:” and “ip4:”. A critical limitation of SPF is the DNS lookup limit of ten queries, which can be problematic for organizations using multiple email services. Understanding email security vulnerabilities in standard email systems and proper email spoofing prevention techniques is crucial for effective implementation.
DKIM (DomainKeys Identified Mail)
DKIM provides message integrity verification through cryptographic signatures. When an email is sent, the outgoing mail server adds a digital signature to the message header using a private key. The recipient’s server then verifies this signature using the corresponding public key published in the sender’s DNS records. This process ensures that the email content hasn’t been altered during transit and confirms the sender’s domain ownership. Complete DMARC implementation guides provide detailed steps for proper DKIM configuration.
The strength of DKIM lies in its use of public-key cryptography, which makes it extremely difficult for attackers to forge valid signatures without access to the private key. Organizations should use key lengths of at least 2048 bits to ensure adequate security. Regular key rotation is also recommended to prevent replay attacks and maintain security over time. The Italian case likely involved domains that either lacked DKIM implementation entirely or had improperly configured DKIM records that didn’t align with DMARC requirements. UK government email security guidance and university research on email authentication security provide comprehensive insights into proper DKIM implementation.
DMARC (Domain-based Message Authentication, Reporting and Conformance)
DMARC serves as the policy enforcement mechanism that builds upon SPF and DKIM to provide comprehensive email authentication. It not only checks whether emails pass SPF and DKIM validation but also verifies that these protocols align with the visible “From” address in the email header. Most importantly, DMARC allows domain owners to specify what action receiving servers should take when emails fail authentication: monitor (p=none), quarantine (p=quarantine), or reject (p=reject). Microsoft’s DMARC configuration guide provides detailed implementation instructions, while the NCSC’s email security check tool helps organizations verify their configurations.
The power of DMARC lies in its reporting capabilities, which provide domain owners with detailed information about who is sending emails on their behalf. These reports help organizations identify legitimate services that need to be authorized and detect unauthorized use of their domains. The gradual enforcement approach allows organizations to start with monitoring to understand their email ecosystem before moving to stricter policies that block spoofed emails. Academic research on email authentication and comprehensive implementation guides provide evidence-based approaches to DMARC deployment.
Government Email Security Vulnerabilities
Government institutions face unique challenges in securing their email communications due to the sensitive nature of their work and the high value they present as targets. The Italian case exemplifies how fragmented IT infrastructure and inconsistent security policies can create vulnerabilities that compromise national security communications. Canadian government email security guidance provides comprehensive best practices for addressing these challenges.
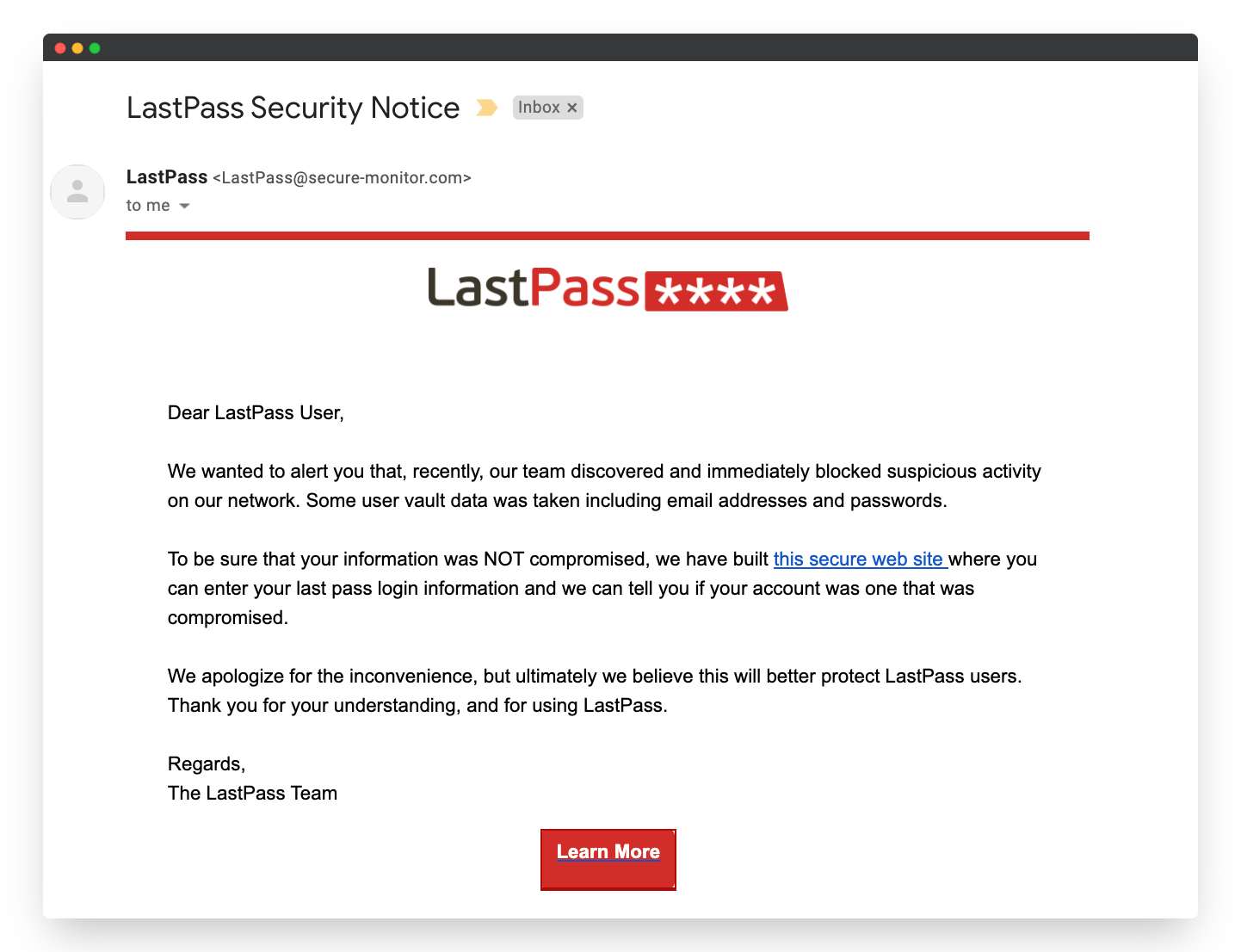
Example of a phishing email disguised as a LastPass security notice designed to steal user credentials.
The research conducted by Andrea Mavilla revealed that the vulnerability affected not just individual government officials but entire institutional domains. This systemic weakness stemmed from what the researcher described as “fragmented infrastructure among multiple providers” with “non-uniform DNS and policies, legacy system inheritance, and governance that is not completely centralized for security configurations”. This fragmentation is common in government environments where different departments and agencies often maintain separate IT systems without coordinated security oversight. The findings align with broader concerns about email domains spoofing vulnerabilities highlighted at major cybersecurity conferences.
Government email systems are particularly attractive targets for several reasons. They contain classified information, national security communications, and sensitive citizen data. State-sponsored attackers often target government agencies to steal intelligence, while criminal groups focus on these systems for financial gain through business email compromise attacks. The consequences of successful attacks can extend far beyond financial losses to include compromised national security, diplomatic incidents, and erosion of public trust. Understanding email authentication methods and implementing email security hardening techniques is crucial for protecting government communications. Comprehensive email security recommendations provide frameworks for addressing these challenges.
Recent statistics show alarming trends in government-targeted cyberattacks. In 2024, Italy experienced a record year for cyber incidents, with the National Cybersecurity Agency recording 1,979 monitored cyber events, representing a significant increase from previous years. The vulnerability in government email systems contributes to this growing threat landscape, as compromised communications can serve as entry points for more sophisticated attacks.
Email Server Security Implementation
Securing email servers requires a comprehensive approach that addresses both technical configurations and organizational policies. The lessons learned from the Italian vulnerability highlight the critical importance of implementing robust authentication mechanisms and maintaining centralized security governance. DKIM best practices provide essential guidelines for proper email authentication implementation.
Infrastructure Hardening
Email server hardening begins with securing the underlying infrastructure and implementing proper access controls. Organizations must configure their mail servers to restrict relay access, preventing unauthorized users from sending emails through their systems. Rate limiting is crucial for preventing spam abuse and denial-of-service attacks, while regular software updates ensure that known vulnerabilities are patched promptly. Comprehensive email hardening guides provide detailed implementation steps for these security measures.
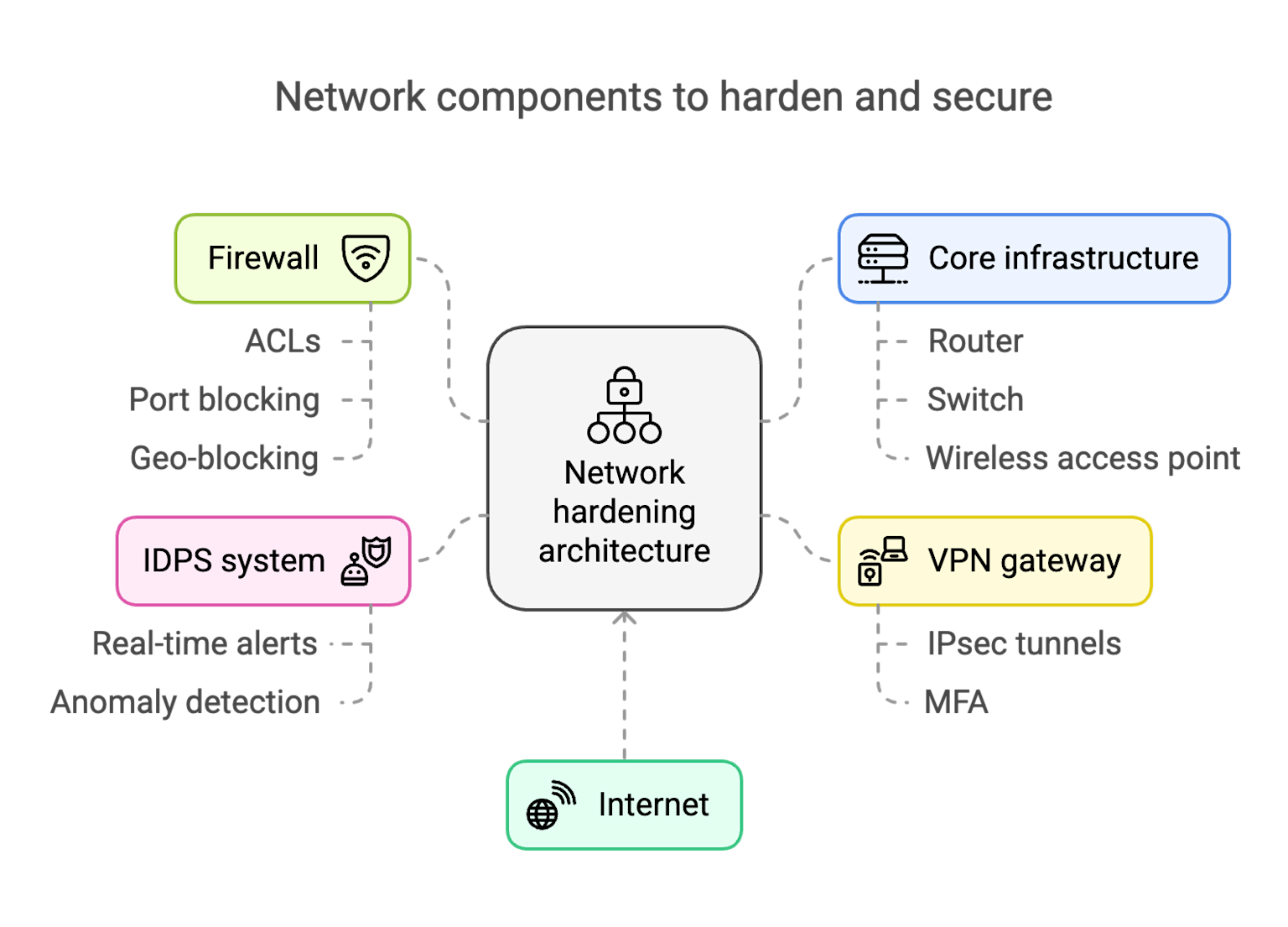
Key network components and strategies used for network hardening to enhance security.
DNS Security Extensions (DNSSEC) provide an additional layer of protection by ensuring the integrity of DNS records. This prevents attackers from tampering with email authentication records like SPF, DKIM, and DMARC policies. While DNSSEC implementation can be complex, it’s essential for preventing DNS-based attacks that could undermine email security measures. New Zealand’s secure government email framework provides comprehensive guidance for implementing these security measures.
Secure Email Gateways (SEGs) serve as the first line of defense against malicious emails. These systems provide spam filtering, malware detection, and data loss prevention capabilities. Advanced SEGs can integrate with Security Information and Event Management (SIEM) systems to provide comprehensive monitoring and threat detection. Organizations should configure SEG policies to block suspicious attachments and links while maintaining detailed logs for forensic analysis. Understanding various email authentication methods and implementing email server security best practices ensures comprehensive protection.
Authentication Protocol Implementation
The implementation of SPF, DKIM, and DMARC requires careful planning and phased deployment. Organizations should begin by conducting a comprehensive audit of their current email authentication status. This assessment helps identify existing gaps and provides a baseline for improvement efforts. Resources on email authentication setup and MDaemon email server security provide practical guidance for this process.
SPF implementation starts with identifying all services that send emails on behalf of the organization. This includes not only primary email servers but also marketing platforms, customer support systems, and any third-party services that send notifications or communications. The SPF record should be configured with appropriate qualifiers: “-all” for strict enforcement or “~all” for soft fail during testing phases. Australian government email security guidelines and secure email authentication setup guides provide detailed implementation instructions.
DKIM deployment requires generating public-private key pairs and configuring the email server to sign outgoing messages. The public key must be published in DNS records using the appropriate selector format. Organizations should use strong key lengths (2048 bits minimum) and implement key rotation procedures to maintain security over time. NinjaOne’s email server security guide and ShareFile’s email security best practices provide comprehensive implementation strategies.
DMARC implementation should follow a gradual approach, starting with monitoring mode (p=none) to collect data about email flows. This allows organizations to identify all legitimate senders and ensure proper authentication before enforcing stricter policies. The transition to quarantine and reject policies should be done carefully to avoid blocking legitimate emails. Twilio’s 5-step email authentication guide and EasyDMARC’s organizational protection strategies provide practical implementation roadmaps.
Advanced Email Security Measures
Beyond basic authentication protocols, organizations should implement additional security measures to create defense in depth. Multi-factor authentication (MFA) for email access provides protection against credential-based attacks. Even if attackers obtain user passwords, they cannot access email accounts without the additional authentication factor.
Transport Layer Security (TLS) encryption ensures that emails are protected during transmission between mail servers. Organizations should configure their systems to require TLS 1.2 or higher and implement Mail Transfer Agent Strict Transport Security (MTA-STS) policies to enforce secure connections. For highly sensitive communications, end-to-end encryption using S/MIME or PGP provides additional protection. Comprehensive guides on mastering email security authentication methods and 2024 email security best practices provide detailed implementation strategies.
Email archiving and monitoring systems help organizations detect and respond to security incidents. These solutions can identify unusual patterns in email traffic, detect potential data exfiltration attempts, and provide forensic capabilities for incident investigation. Integration with threat intelligence feeds enhances the ability to identify and block known malicious actors. Understanding email monitoring regulations in Italy and EU email security mandates is crucial for compliance.
International Standards and Best Practices
Government organizations worldwide are implementing standardized approaches to email security. The UK’s Government Cyber Security Policy requires all government domains to implement DMARC, SPF, and DKIM authentication. The policy also mandates TLS encryption for email transport and regular monitoring of authentication reports. Reports show that phishing campaigns continue to spoof government agencies, highlighting the ongoing need for robust security measures.
European Union initiatives are pushing for harmonized email security standards across member states. The NIS2 Directive presents opportunities for mandating stronger email security protocols like DMARC, DKIM, and SPF across all EU countries. Several member states, including Denmark, Ireland, and the Netherlands, have already implemented requirements for government bodies to deploy these authentication protocols. Recent GDPR fines related to email metadata privacy breaches demonstrate the increasing regulatory focus on email security. Additionally, certified email standards like REM are becoming the new European standard for secure communications.
The United States has established comprehensive email security requirements through various federal mandates. The Cybersecurity and Infrastructure Security Agency (CISA) provides detailed guidance on implementing email authentication protocols and requires federal agencies to deploy DMARC enforcement policies. These standards serve as models for other countries developing their own email security frameworks. New Zealand’s protective security guidance on email fraud and Italian regulatory developments regarding corporate email usage show how different countries are addressing email security challenges.
Lessons from the Italian Case
The Italian government email vulnerability provides several critical lessons for organizations worldwide. First, it demonstrates that fragmented IT infrastructure creates security gaps that can be exploited by sophisticated attackers. Organizations must implement centralized governance for email security to ensure consistent policy enforcement across all domains and systems. Comparative studies of email security in Europe show varying levels of implementation across different countries.
Second, the case highlights the importance of proactive security testing. The vulnerability existed because proper authentication protocols were not implemented or were incorrectly configured. Regular security audits and penetration testing can identify these gaps before they’re exploited by malicious actors. Guidance on investigating government cyber attacks provides methodologies for proactive security assessment.
Third, the incident underscores the need for comprehensive security awareness training. While technical measures are essential, human factors play a crucial role in email security. Users must be trained to recognize spoofing attempts and understand proper procedures for verifying suspicious communications. Additional cybersecurity insights from Italy’s 2024 ACN report and public sector phishing awareness guides provide comprehensive training frameworks.
Implementation Roadmap
Organizations seeking to improve their email security should follow a structured implementation approach. The first phase involves conducting a comprehensive security assessment to identify current vulnerabilities and establish baseline measurements. This assessment should include testing of existing authentication protocols, evaluation of email server configurations, and analysis of current security policies. Italian cybersecurity analysis reports from Clusit 2024 and UK council case studies provide frameworks for conducting these assessments.
The second phase focuses on implementing basic authentication protocols, starting with SPF records for all domains. Organizations should then deploy DKIM signing for outbound emails and enable TLS encryption for email transport. These foundational measures provide immediate security improvements while preparing for more advanced implementations. Detailed cybersecurity analysis from Italian sources and European certified email standards like PEC provide implementation guidance.
The third phase involves DMARC deployment, beginning with monitoring mode to collect data about email flows. Organizations should analyze DMARC reports to identify all legitimate senders and ensure proper authentication before transitioning to enforcement policies. This gradual approach minimizes the risk of blocking legitimate emails while building confidence in the authentication system. Reports from CERT-AGID on annual cyber attacks and EU MFA regulatory mandates provide regulatory context for these implementations.
The final phase includes advanced security measures such as threat intelligence integration, advanced persistent threat detection, and comprehensive security monitoring. Organizations should also establish incident response procedures and conduct regular security assessments to maintain their security posture. Public sector phishing awareness resources and Clusit 2024 cybersecurity analysis provide frameworks for ongoing security management.
Future Considerations
The email security landscape continues to evolve as attackers develop new techniques and technologies. Artificial intelligence is being used both by attackers to create more convincing phishing emails and by defenders to detect sophisticated threats. Organizations must stay current with emerging threats and adapt their security measures accordingly. European digital identity framework developments and EU internet standards for email are shaping the future of secure communications.
Emerging standards like Brand Indicators for Message Identification (BIMI) provide additional layers of authentication by displaying verified brand logos in email clients. While not yet widely adopted, BIMI represents the future direction of email authentication, providing visual cues to help users identify legitimate communications.
The integration of email security with broader cybersecurity frameworks is becoming increasingly important. Organizations must consider email security as part of their overall security architecture, ensuring that email protection measures integrate effectively with other security controls and monitoring systems.
The vulnerability discovered in the Italian government’s email system serves as a powerful reminder that email security cannot be taken for granted. As demonstrated by this case, even the most sensitive communications remain vulnerable when proper authentication mechanisms are not implemented or correctly configured. The solution lies not just in deploying technical measures but in establishing comprehensive security governance that ensures consistent implementation and maintenance of email security protocols across entire organizations.
The path forward requires commitment to implementing robust email authentication protocols, establishing centralized security governance, and maintaining vigilant monitoring of email systems. Organizations that fail to address these fundamental security requirements do so at their own peril, potentially exposing themselves to the same type of vulnerability that compromised the Italian government’s communications. The time for action is now, before the next headline-grabbing security incident exposes another organization’s inadequate email security measures.