Hidden metadata reveals what your iPhone silently records about you
A recent forensic analysis by cybersecurity researcher Elorm Daniel uncovered a startling reality: iPhones continuously log detailed metadata that most users never see, including precise GPS coordinates from messages, complete password histories, and group memberships that persist even after users leave. This discovery raises critical questions about digital privacy and what our devices really know about us.
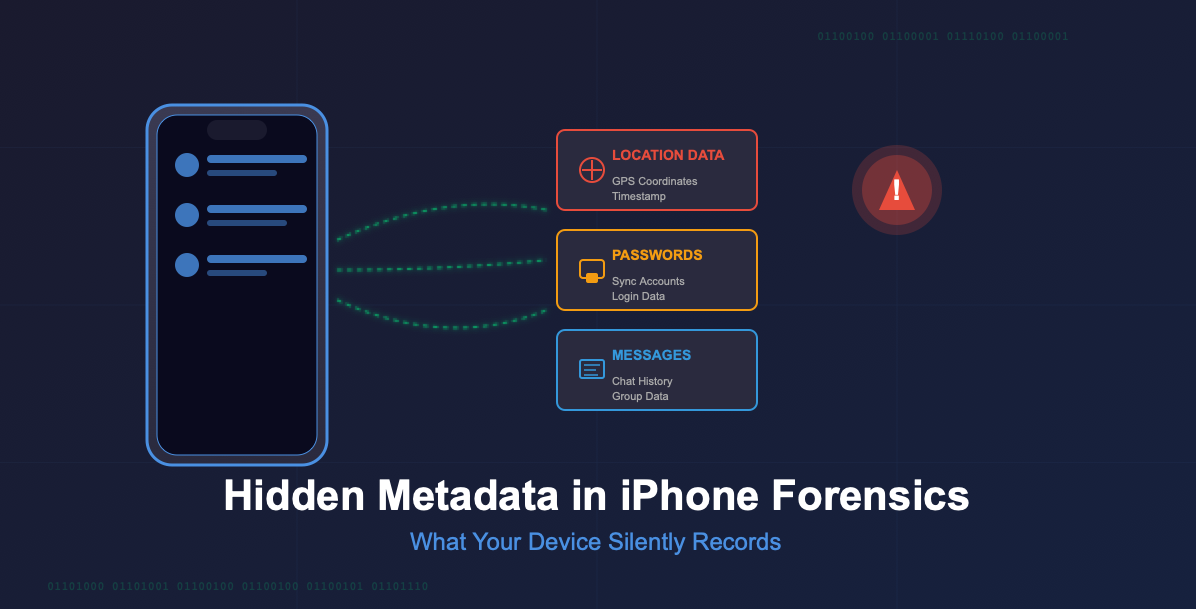
When Elorm Daniel performed a routine forensic extraction on his iPhone 12 Pro Max, he expected to find the usual suspects like messages, photos, and call logs. What he discovered instead was far more revealing. The device had been silently recording an extensive digital trail that painted an incredibly detailed picture of his life, movements, and connections. Perhaps most unsettling was the discovery that a seemingly innocent WhatsApp message from a colleague contained hidden location data, even though neither party had intentionally shared their whereabouts.
Daniel shared his findings in a detailed thread on X (formerly Twitter), where he documented the complete scope of data recovered from his device. This wasn’t the result of sophisticated hacking or a jailbroken device. Everything Daniel uncovered came from a standard, non-jailbroken iPhone using professional forensic tools commonly employed by law enforcement and investigators worldwide. The implications are profound: every iPhone user is creating a comprehensive digital footprint that extends far beyond what appears on their screen.
The invisible location tracker in your pocket
The most striking revelation from Daniel’s research centered on location tracking. While examining messages he received on September 3, 2025, at 7:11 AM, he found something unexpected. The message from his colleague appeared normal on the surface, just a regular text conversation. But buried within the message metadata, his iPhone had silently logged the sender’s exact GPS coordinates at the moment the message was sent.
This automatic location logging extends beyond messages. Every photo, video, screenshot, and recording created on the device carries embedded GPS coordinates marking exactly where the user was when that file was created. This level of granularity allows investigators to reconstruct complete movement patterns, timelines, and behaviors with remarkable accuracy. The EXIF metadata embedded in these files creates an unintentional but precise breadcrumb trail of a person’s daily life.
What makes this particularly significant is that users have virtually no awareness this is happening. While many people know that photos contain location data if geotagging is enabled, few realize that their messages are also carrying location information about both sender and recipient. The forensic extraction revealed that if location services are active during WhatsApp conversations, precise coordinates can be recovered from someone else’s device during forensic imaging, even if you never explicitly shared your location.
Beyond messages and what forensic tools really uncover
The location data was just the beginning of what Daniel’s forensic analysis revealed. The extraction pulled comprehensive account credentials, including synchronized passwords, usernames, URLs, and stored login metadata. Every password ever used on the device was recoverable without requiring a jailbreak, challenging common assumptions about iOS security and data protection.
Application logs presented another layer of exposure. Every installed app, even those marketed as secure or encrypted, left behind detailed usage histories, internal data, and metadata. These digital traces persist long after users believe they’ve deleted information or uninstalled applications. The forensic tools could reconstruct app activity patterns, revealing when applications were used, what actions were performed, and how users interacted with different services.
WhatsApp data proved especially revealing. Daniel discovered that his device maintained a complete history of every group he had ever joined, including creation dates, creator identities, the exact date he was added, and detailed metadata that persisted even after leaving groups. This information becomes particularly critical in investigations, as suspects cannot plausibly deny group membership when the device itself retains creation dates, creator identity, join dates, and complete participation timelines, even if they exited the group years ago.
The message-level location metadata extended to showing exact sender locations at the moment messages were typed and sent. Most users never see this information in their day-to-day use, but forensic investigators routinely access it during examinations. This creates an asymmetry of knowledge where users operate under one set of assumptions about their privacy while their devices tell a completely different story to those with the right tools.
The persistence of digital memory
One of the most significant findings from Daniel’s research relates to data persistence. Digital devices, particularly smartphones, rarely forget information even when users believe they have deleted it. The forensic extraction demonstrated that supposedly removed data often remains recoverable through standard investigative techniques.
This persistence extends across multiple data categories. Deleted messages often leave traces in database files, backup records, or cache locations. Group memberships, even for groups exited long ago, remain documented in the device’s internal records. Application data continues to exist in various forms even after apps are uninstalled. The iPhone’s internal file system maintains detailed logs that users cannot easily access or erase through normal device use.
The implications for privacy are substantial. Users making privacy decisions based on what they can see on their screens operate with incomplete information. The actual data retained by their devices extends far beyond the visible interface. This gap between user perception and technical reality creates vulnerabilities that individuals may not anticipate or understand.
From a security perspective, this persistent data storage serves legitimate purposes. Forensic investigators can use this information to solve crimes, identify suspects, and reconstruct events. However, it also means that anyone with physical access to a device and appropriate tools can potentially recover years of detailed personal information, regardless of what the device owner has attempted to delete or conceal.
The broader implications for digital privacy
Daniel’s findings raise fundamental questions about the balance between functionality, security, and privacy in modern smartphones. The metadata collection he documented isn’t the result of malicious software or security vulnerabilities. These are features built into iOS and similar operating systems, designed to enhance user experience, enable synchronization across devices, and support various applications and services.
However, most users lack awareness of the extent of this data collection. The iOS privacy controls that Apple provides focus primarily on preventing third-party apps from accessing user data, not on limiting what the operating system itself records. Users can disable location services, limit app permissions, and control various privacy settings, but these controls don’t eliminate the fundamental metadata generation that occurs during normal device operation.
The research also highlights the evolution of digital forensics. Modern forensic tools can extract remarkable amounts of information from non-jailbroken devices, challenging the notion that strong passcodes and device encryption provide complete protection against data access. While these security measures do offer important protections, they may not prevent forensic recovery of data from devices that are unlocked or have been properly imaged by investigators.
Legal and ethical considerations emerge from this technical reality. Law enforcement agencies worldwide increasingly rely on mobile device forensics to investigate crimes, often accessing exactly the kind of metadata Daniel documented. Privacy advocates argue that this level of data availability raises concerns about surveillance, particularly when combined with other information sources. The question becomes not whether this data exists, but who should have access to it and under what circumstances.
Understanding your digital footprint
The research conducted by Elorm Daniel serves as a wake-up call for anyone who uses a smartphone. Every device tells a story through the digital trails it creates and preserves. Messages carry more than text, photos contain more than images, and app usage leaves more traces than most users realize. The comprehensive nature of this metadata collection means that investigators can reconstruct detailed timelines of activities, associations, and locations, often going back years.
For the average user, this reality demands a reassessment of digital privacy assumptions. While completely eliminating metadata generation remains impractical without severely limiting device functionality, understanding what information devices collect represents an important first step. Users concerned about privacy might consider disabling location services when not needed, regularly reviewing app permissions, being mindful of what data they synchronize across devices, and recognizing that deleted doesn’t always mean permanently erased.
The forensic extraction demonstrated that even without jailbreaking, professional tools can discover locations, passwords, group associations, message histories, detailed app activity, and metadata that most users never realize exists. This isn’t about creating paranoia around technology use, but rather fostering informed decision-making about digital privacy. As Daniel’s research clearly shows, our devices rarely forget, even when we do.