Maritime cyber rules are coming, are you ready?
Why the sea is now a digital border
Maritime transport has spent a decade chasing efficiency through digitization, automation, and end‑to‑end visibility. Today, a ship depends on software as much as it depends on steel, and a port behaves like a data center with cranes. Navigation systems and shore coordination increasingly rely on remote access and satellite connectivity. The gain is real, but the bill arrives in a different currency: cyber risk that can spill into physical consequences.
The argument, laid out clearly in Cyber Security Italia through the lens of a new “Maritime Cyber Risk” initiative, is not that shipping suddenly discovered hackers. It is that the sector has finally admitted something many operators already knew: safety and security now share the same failure modes. When a terminal scheduling system fails, the impact is not just an IT outage, it becomes delayed departures and congested routes that reach insurers and regulators.
In Genoa, Trieste, and other strategic ports, the risk does not respect organizational charts. It moves along the same paths as routine work: email accounts used by agents, remote maintenance sessions, shared credentials, and integrations with suppliers.
What regulators are actually asking for
Regulation in shipping tends to arrive after practice has changed, and cybersecurity is following that pattern. The maritime world already knows how to run a disciplined safety culture through management systems, inspections, and shared rules. The novelty is that cyber risk is being treated as an input to that culture, not an optional technical footnote.
At the international level, the IMO has been pushing the idea of cyber risk management as part of the broader safety culture, and its Guidelines on maritime cyber risk management frame the topic around outcomes rather than vendor checklists. In parallel, Europe is raising the floor through stronger governance and reporting expectations, and the NIS2 Directive makes resilience a board-level duty, not merely an IT budget line.
The Italian move, described in the same Cyber Security Italia analysis, is more concrete: a new circular on “Maritime Cyber Risk” with an effective date of 1 November 2026, designed to give the ecosystem a common reference point for operators and authorities. The official framing is available through the Guardia Costiera via its navigation and maritime safety regulatory hub, and it matters because it translates principles into expectations.
This is where many companies misunderstand the moment. The goal is not to drown shipping in paperwork, it is to standardize a minimal set of behaviors that reduce surprise. In practice, it means being able to show that risk is assessed continuously, that responsibilities are explicit, and that evidence of control exists even under stress.
Where companies sabotage their own compliance
The hardest part of maritime cybersecurity is not writing a policy, it is keeping your story credible when operations become chaotic. The threat categories are not exotic: broad malware campaigns coexist with targeted intrusions, and attackers range from accidental actors to disgruntled insiders and well-resourced groups. The fragility sits in the intersections, where interconnected operations meet shared access paths.
A major incident can start in the shore office and end on a vessel, or start in a port service provider and cascade across multiple operators. The 2017 Maersk disruption is a reminder that one compromise can create a shared blast radius across logistics. That pattern is reinforced by how adversaries exploit identity, remote access, and third parties, as described in the ENISA threat landscape through recurring themes like credential theft and supply-chain exposure.
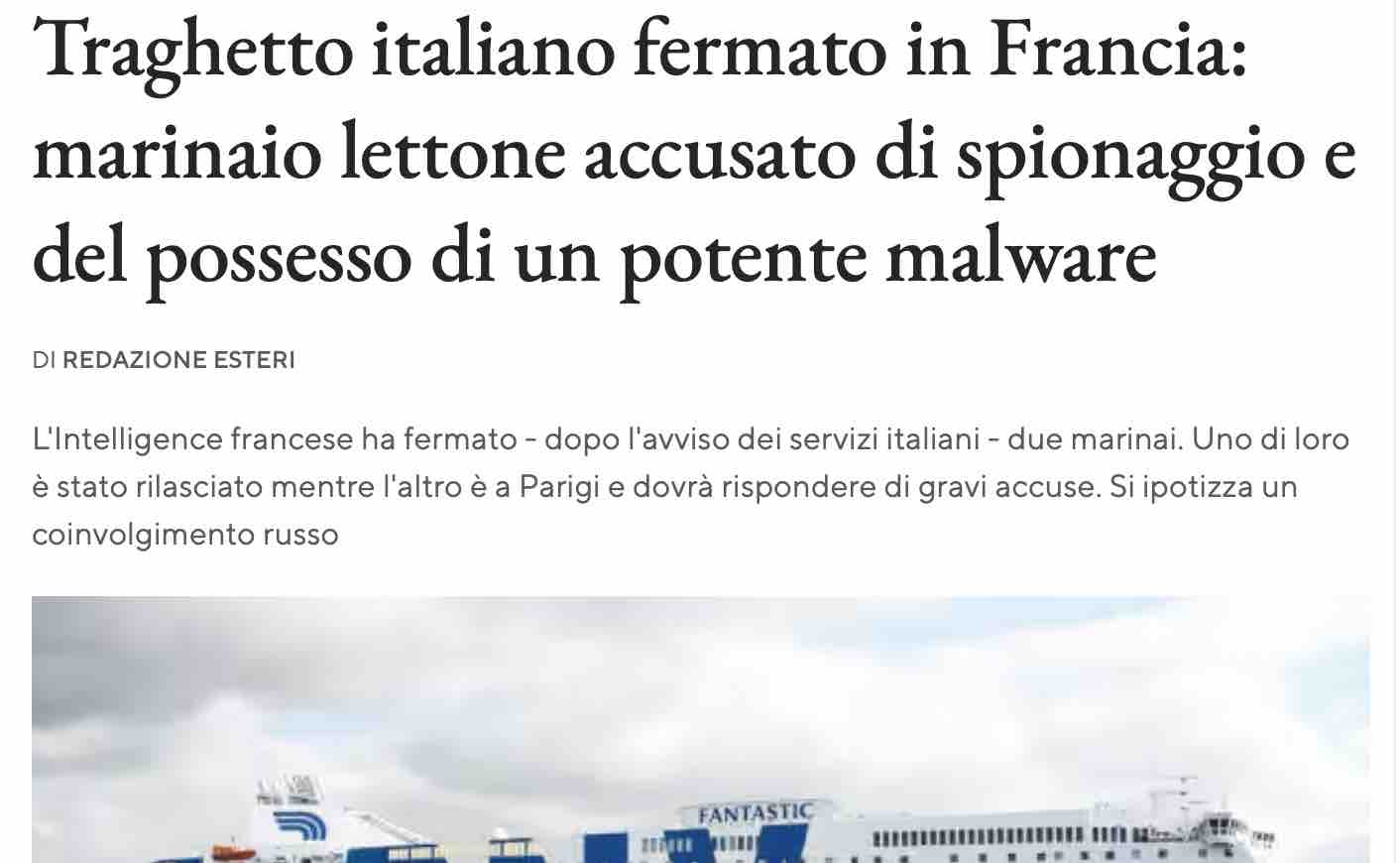
That is not abstract. In December 2025, an Italian ferry owned by GNV was held in the French port of Sète during a search triggered by an alert from Italian intelligence; a crew member was accused of carrying a device with a RAT, a remote access tool, that investigators believed could be used to control the vessel’s systems from a distance, as Il Fatto Quotidiano reported from Paris.
Now to the part the sector rarely admits in public: culture routinely undermines compliance. Many organizations will publish glossy pages about being inclusive and agile, then run workplaces where speaking up is risky and “agile” becomes hurry up and absorb the damage later. Security staff are told to “move fast” without authority to stop unsafe changes.
In Rotterdam or Naples, that hypocrisy looks the same: a vendor contract that rewards delivery dates over hardening, a management chain that prefers reassuring dashboards to uncomfortable truth. When people learn that the safest career move is to stay quiet, you lose psychological safety, and early warnings disappear.
How to turn rules into resilience before 2026
The 2026 effective date is not an invitation to procrastinate, it is an opportunity to practice. Maritime organizations that wait for audits to force change will end up implementing controls under pressure. A more realistic approach is to treat regulation as a forcing function for discipline.
That starts with leadership choices. If executives want measurable resilience, they have to make it rational for people to speak up early. They have to fund inventory and access control work that is tedious but decisive. A culture that claims inclusion while normalizing exhaustion will not retain the defenders it needs.
Frameworks help, but only when they are used as instruments rather than slogans. The NIST Cybersecurity Framework is useful because it makes outcomes discussable across functions, and it forces organizations to connect protect, detect, respond, and recover as one system.
If there is one practical test that cuts through the noise, it is whether a company can demonstrate that it can detect an intrusion, contain it, and restore operations with tested assumptions. When that capability exists, regulation becomes documentation of reality. When it does not, regulation becomes a performance.