Fake recruiters weaponize job offers to target cryptocurrency developers
A sophisticated cyber campaign orchestrated by the North Korean Lazarus Group is using fake job opportunities to compromise cryptocurrency developers worldwide. Security researchers at ReversingLabs have uncovered a complex operation that blends social engineering with malware distribution through trusted open-source repositories, marking a dangerous evolution in supply chain attacks.
The anatomy of a digital deception
The campaign, dubbed graphalgo by researchers, has been active since May 2025 and operates through an intricate web of fake companies, malicious code packages, and professional-looking recruitment efforts. At the heart of the operation lies Veltrix Capital, a fabricated blockchain and cryptocurrency trading firm complete with a polished website displaying corporate vision statements and mission descriptions. The domain was registered in April 2025, and the attackers created corresponding GitHub repositories to lend credibility to their scheme.
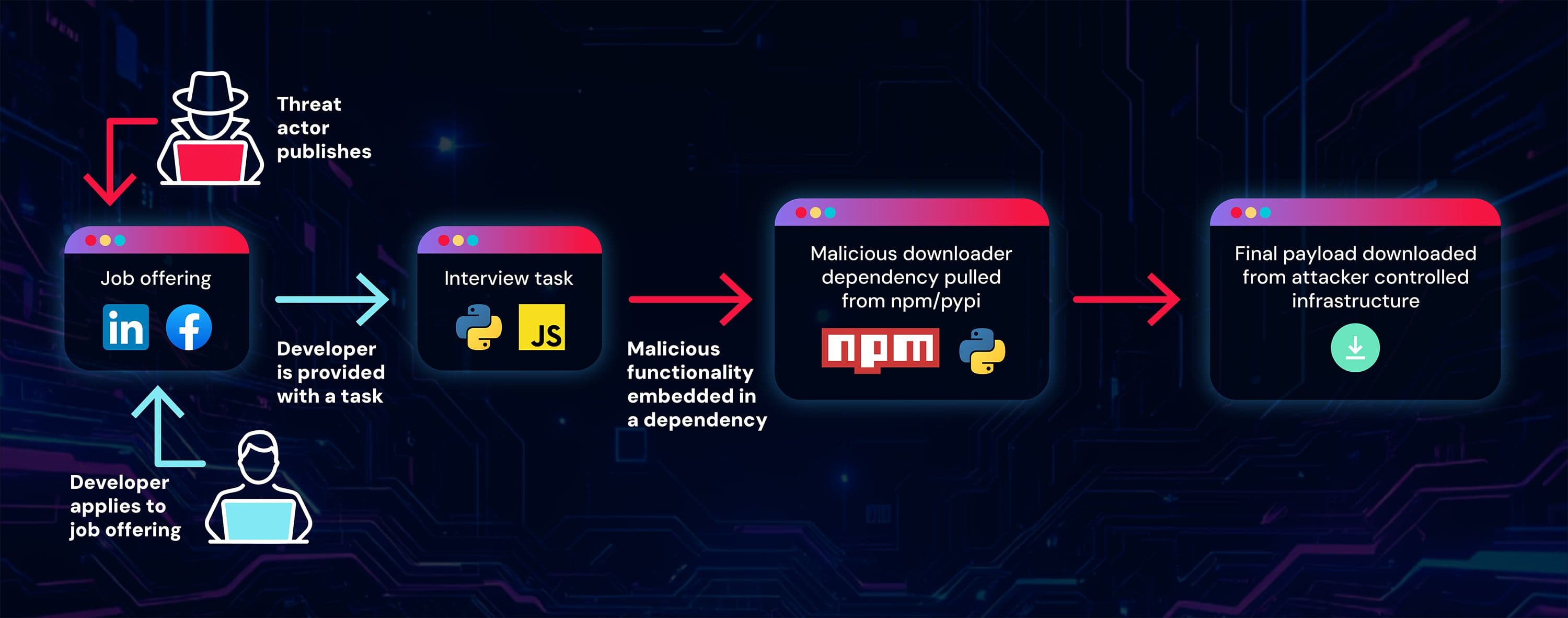
Developers are contacted through multiple channels including LinkedIn, Facebook, and specialized forums like Reddit. The recruitment pitch appears legitimate, offering DevOps and developer positions with what seem like standard coding challenges. However, these technical assessment tasks contain hidden dangers. When candidates download and run the interview projects, they unknowingly install malicious dependencies embedded within npm and PyPI packages, triggering a chain of infections on their systems.
Modular architecture enables persistent threats
What distinguishes this campaign from previous attacks is its modular design that separates the social engineering “frontend” from the malware distribution “backend.” The attackers created legitimate-looking repositories named test-url-monitoring, test-devops-monitoring, and test-devops-orchestrator across both Python and JavaScript environments. These repositories appear harmless on the surface, but their package.json and requirements files reference dependencies with names like graphnetworkx and bigmathutils that masquerade as popular libraries.
The malicious packages impersonate legitimate tools such as graphlib for npm and networkx for PyPI. One particularly concerning case involved the bigmathutils package, which remained benign for over a month while accumulating more than 10,000 downloads. Only in February 2026 did the attackers release version 1.1.0 containing the malicious payload, demonstrating patience and strategic timing designed to build trust before striking. This tactic allowed the malware to reach a substantial user base before detection systems could identify the threat.
Multi-stage payload delivery and RAT deployment
Once installed, the malicious packages function as downloaders for second-stage payloads. The final component is a remote access trojan (RAT) that establishes persistent communication with command-and-control servers at domains like codepool[.]cloud and aurevian[.]cloud. The RAT supports standard espionage capabilities including file upload and download, process enumeration, and arbitrary command execution. Notably, the malware specifically checks for the Metamask browser extension, a clear indicator that the attackers are targeting cryptocurrency wallets and digital assets.
The campaign deployed three functionally identical RAT versions written in JavaScript, Python, and VBScript, demonstrating the threat actors’ versatility and commitment to cross-platform compromise. Communication with C2 servers employs token-based authentication, a technique previously observed in North Korean state-sponsored operations. This security measure prevents researchers from easily analyzing C2 traffic without valid credentials obtained during the initial infection phase.
Attribution and ongoing evolution
Multiple technical indicators point to the Lazarus Group as the perpetrator behind this campaign. Git commit timestamps consistently show GMT+9 timezone activity, corresponding to North Korean working hours. The techniques mirror previous Lazarus operations, including the 2023 VMConnect campaign that also used fake recruiter scenarios and malicious PyPI packages. The modular approach, cryptocurrency focus, and sophisticated multi-layer obfuscation all align with the advanced persistent threat group’s known tactics.
Research teams have identified connections between the “graph” series packages and Veltrix Capital recruitment efforts, but evidence suggests additional undiscovered campaigns exist. The “big” series packages and the VBScript RAT variant have no clear connection to identified frontend operations, indicating that multiple recruitment schemes are operating simultaneously. This reveals an ongoing, large-scale operation with no signs of stopping. The attackers can rapidly deploy new fake companies and job postings while maintaining the same technical infrastructure, making detection and disruption significantly more challenging for defenders.
Protecting development environments from social engineering
Organizations employing software developers must implement multi-layered defenses against these sophisticated attacks. Developer workstations should operate with restricted network access and mandatory code review processes before running any external projects. Package management tools should employ strict verification mechanisms, and dependency installations should trigger security alerts for manual review. Training programs must educate developers about social engineering tactics, particularly those involving recruitment offers that seem unusually attractive or require immediate code execution.
The cryptocurrency and blockchain sectors face heightened risk given the direct financial motivation behind these attacks. Companies should establish verified communication channels for recruitment processes and maintain up-to-date threat intelligence on known malicious packages. Regular security audits of development environments, combined with network monitoring for suspicious outbound connections, provide critical detection capabilities. As state-sponsored groups continue refining their tactics, the security community must remain vigilant and share intelligence rapidly to protect the open-source ecosystems that underpin modern software development.
IoCs
I have prepared a curated STIX 2.1 file with IoCs that can be imported into your SIEM or threat hunting platform. The file is available here.